CVE-2024-27716 - Cross-site Scripting (XSS) in Eskooly Web Product <= v3.0

Introduction
Cross-Site Scripting (XSS) vulnerabilities are a common and serious threat to web applications, allowing attackers to inject malicious scripts into web pages viewed by other users. This post explores CVE-2024-27716, a critical XSS vulnerability in Eskooly Web Product v.3.0 that enables attackers to execute arbitrary code via message sending and user input fields.
Discovery of the Vulnerability
A Cross-Site Scripting (XSS) attack consist in the injection of malicious scripts in websites pages. Such attack is useful to execute attacker stored malicious code, generally in the form of a browser side script, in a victim browser when this latter is viewing the affected page. Several XSS payloads exists to steal victim cookies or any other legitimate user browser information.
In the application:
it is possible to trigger a malicious XSS through messages send to Admin or Teacher (to steal a cookie for example), it’s a STORED XSS.
it is possible to trigger a reflected XSS through a lot of boxes (student name, phone number, teacher,…)
Related Findings
Cross-Site Scripting (XSS)
Stored XSS
Reflected XSS
Technical Details
The vulnerability arises from insufficient input sanitization and validation. Specifically, user inputs are not properly escaped or sanitized before being included in the HTML content of web pages, allowing attackers to inject and execute malicious scripts.
Stored XSS
Shows an attacker (teacher or student for example) crafting a message with a malicious script that is designed to be stored and later executed.
The payload:
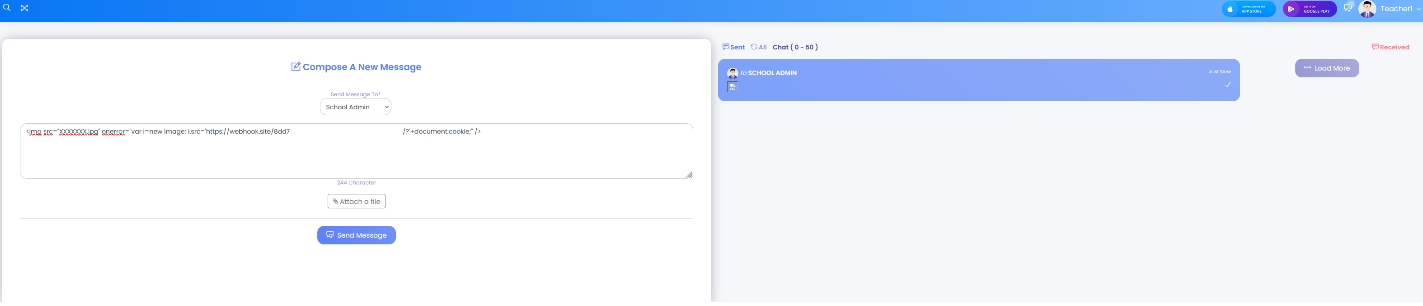
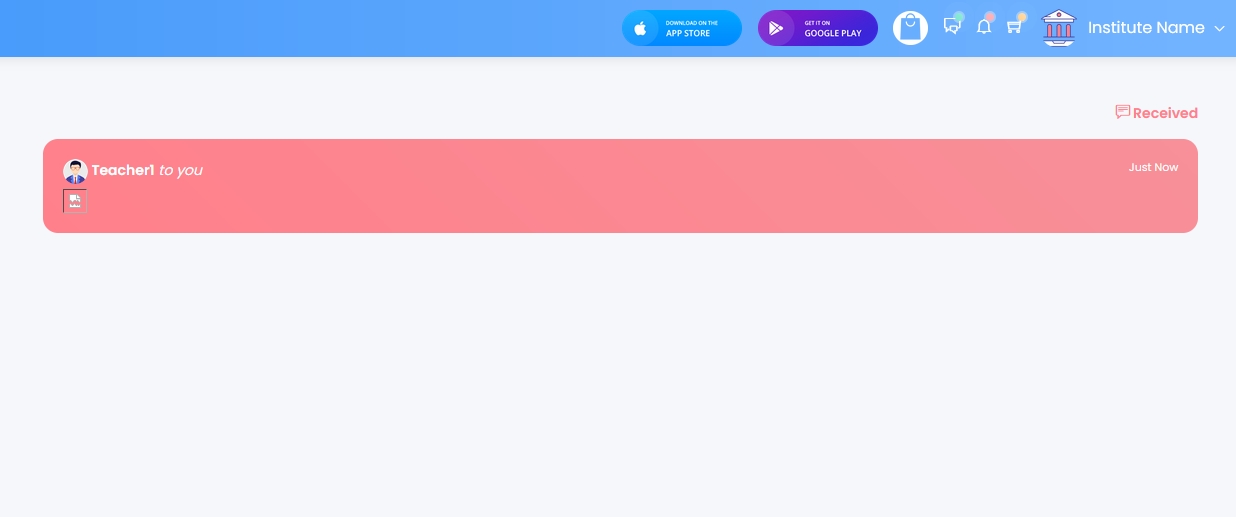
Admin received the message
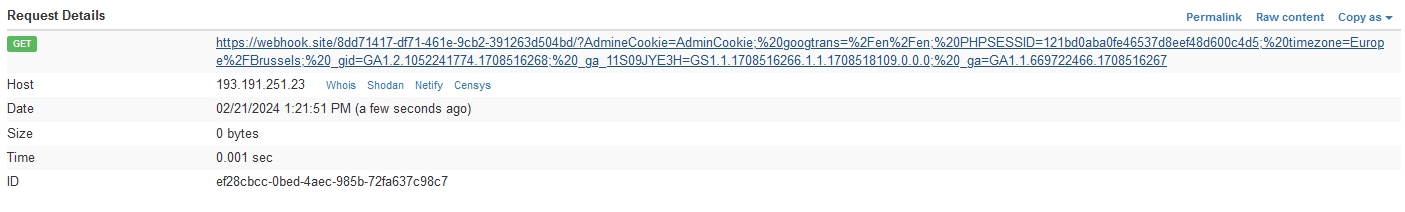
The request details of the stored XSS payload show that a request was made to an external domain, indicating that the malicious script has been executed and data, such as cookies, might have been exfiltrated.
Also, the server does not appear to set any flags on the cookie, such as HttpOnly or Secure, which are critical for protecting the cookie from being accessed by client-side scripts or transmitted over non-HTTPS connections. (See CVE-2024-27713)
Reflected XSS
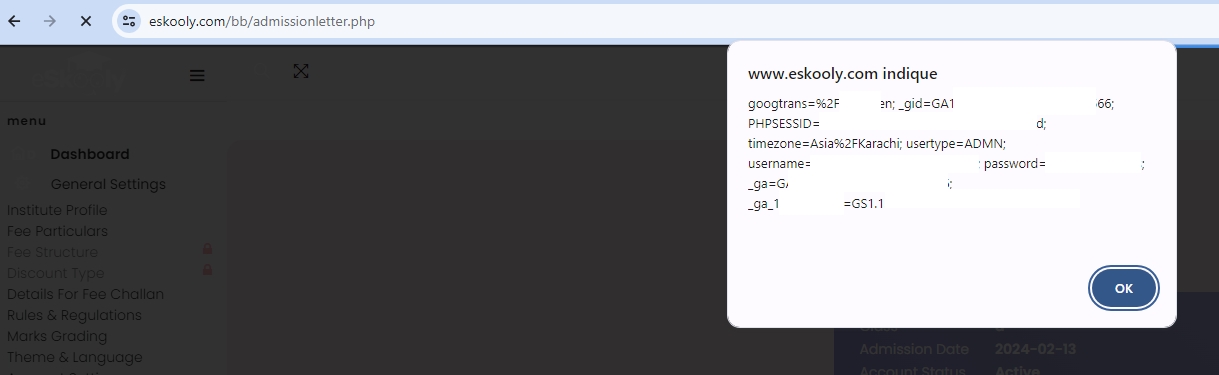
An alert box displays sensitive session information, indicating that the script execution can access and potentially exfiltrate user data.
Risk
Impact
High.
The attacker could potentially perform actions on behalf of the victim, access sensitive information, and compromise user accounts.
Likelihood
High.
The likelihood of exploitation for a XSS vulnerability is high due to its remote exploitability, low attack complexity, lack of required privileges, and the prevalence of known exploits. Especially in the context of the application, where it's possible to steal admin or teacher cookies as student.
Recommendation
It's recommended to implement rigorous user input validation to treat all inputs as untrustworthy and apply strict semantic and syntactic checks, use data pattern whitelists and blacklists, and uniformly sanitize data from all users. Additionally, encoding dynamic content in HTTP responses is crucial to prevent misinterpretation as executable content, with special characters converted to HTML entity encodings for safe processing. Furthermore, deploying a robust Content Security Policy (CSP) is essential to control script sources and execution on web pages, thereby effectively mitigating potential reflected XSS attacks.