CVE-2024-27710 - Privilege Escalation via Authentication Mechanism in Eskooly Web Product <= v3.0
Introduction
A brute force attack involves systematically trying various password combinations against a server. Methods include dictionary and traditional brute-force attacks, using different character sets. The attack's duration depends on the chosen method and the efficiency of both attacking and targeted systems.
This attack is particularly effective against applications with weak security, such as those with poor password policies, no account lockout after multiple failed attempts, and no multi-factor authentication. These vulnerabilities allow attackers to persistently guess passwords, increasing the likelihood of a successful breach, in the Eskooly application.
Discovery of the Vulnerability
CVE-2024-27710 was discovered during a security assessment of Eskooly’s authentication processes. The issue was identified as part of the broken authentication findings, particularly related to the lack of multi-factor authentication (MFA) and weak password policies.
Related Findings
Brute Force Attack
Weak Password Policy
No Account Lockout
Technical Details
The vulnerability arises from insufficient security measures in the authentication process. Specifically, the absence of MFA and the use of weak passwords allow attackers to exploit authentication mechanisms. Attackers can perform brute-force attacks or use session hijacking techniques to gain unauthorized access.
Login password
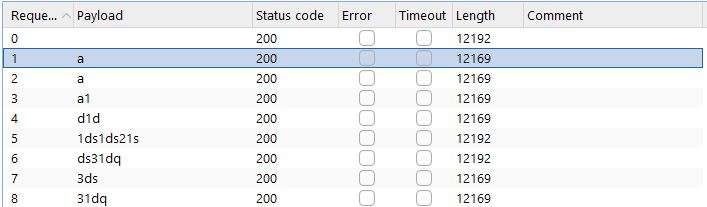
Preparation of the attack: Capture the POST request to signin
Now check the difference between bad password and the right one:
Bad Password
Status code 200 and 12169 < Length < 12192
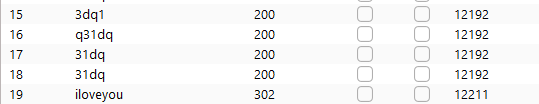
Correct password
Status code 302-Found and Length < 12169
Risk
Impact
Critical.
If an attacker successfully guesses a user's password due to the lack of an account lockout policy, the impact can be considerable. The attacker would gain unauthorized access to the user's account, employees or admin. This unauthorized access could lead to data breaches, identity theft, and other malicious activities. The impact is heightened by the potential for the attacker to access not just a single account, but multiple accounts, especially if password practices across users are weak or uniform.
Likelihood
High.
The absence of an account locking mechanism, combined with weak password policies and the absence of multi-factor authentication, considerably increases the probability of a successful brute force attack. The attacker, who is not bothered by the threat of account locking, can relentlessly attempt to guess the password, a situation further accentuated by simplistic or predictable passwords. The ease with which these attacks can be carried out, often using automated tools, further amplifies the risk of security breaches.
Recommendation
It's recommended to:
Implement a robust account lockout policy: After a certain number of unsuccessful login attempts, the account should be temporarily locked. This prevents continuous password guessing by an attacker.
Enforce strong password policies: Require complex passwords that include a mix of uppercase and lowercase letters, numbers, and special characters. Regularly prompt users to change their passwords and prevent the reuse of old passwords.
Enable multi-factor authentication (MFA): Adding an additional layer of security beyond just a password significantly reduces the risk of unauthorized access. Even if a password is compromised, the attacker would still need the second factor to gain access.
Monitor and limit login attempts: Keep track of failed login attempts and set a threshold after which additional security measures are triggered, such as CAPTCHA verification or requiring additional authentication.
Implement network-level security measures: Use firewalls and intrusion detection systems to monitor and block repeated login attempts from the same IP address.