CVE-2024-27712 - User Enumeration via Account Settings in Eskooly Web Product <= v3.0
Introduction
Username enumeration is a common application vulnerability which occurs when an attacker can determine if usernames are valid or not. Most commonly, this issue occurs on login forms, where an error like “the username is invalid” is returned.
In this context, a student could enumerate VALID teacher account and using the CVE-2024-27710 he will escalate his/her privilege in the application.
Discovery of the Vulnerability
CVE-2024-27711 was identified during a thorough security assessment of Eskooly’s user management and sign-up processes. The issue was found in the account settings where attackers could exploit the sign-up function to gain unauthorized access.
Related Findings
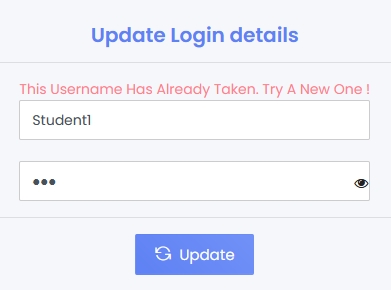
User Enumeration
Technical Details
The vulnerability arises from flaws in the sign-up process that allow attackers to manipulate account settings during registration. This can lead to unauthorized privilege escalation, enabling attackers to register accounts with higher privileges than intended.
User enumeration during the Sign up
It’s possible to enumerate admin account
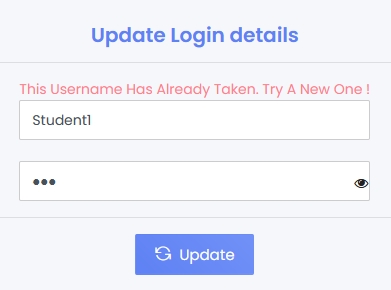
Using this information and the findings related to CVE-2024-27710, a user/student could escalate his/her privilege and get admin access.
Risk
Impact
Medium.
The impact is high as the enumeration itself doesn't grant access but with all broken authentication vulnerabilities increases the risk of targeted attacks.
Likelihood
High.
Username enumeration in the Eskooly Web application is highly likely due to the explicit error message indicating existing usernames. Attackers can easily use this information to identify valid user accounts, which is a preliminary step in many attack vectors.