The FBI dismantles Raptor Train: A Chinese Botnet that Infected 260,000 IoT Devices Worldwide!

Raptor Train is a sophisticated and large-scale botnet active since May 2020. It has compromised more than 260,000 IoT devices and small business networks, including routers and IP cameras. This botnet is attributed to the Chinese state hacker group Flax Typhoon, known for its cyberespionage campaigns targeting critical infrastructure in the United States, Taiwan and other countries. This group uses a complex, multi-layered botnet architecture, making it a persistent threat that is difficult to eradicate.
⏩ For those who are not familiar with the technical terms, do not hesitate to consult the “Definition” chapter otherwise continue the article directly with the “Raptor Train Operation and Infrastructure” chapter.
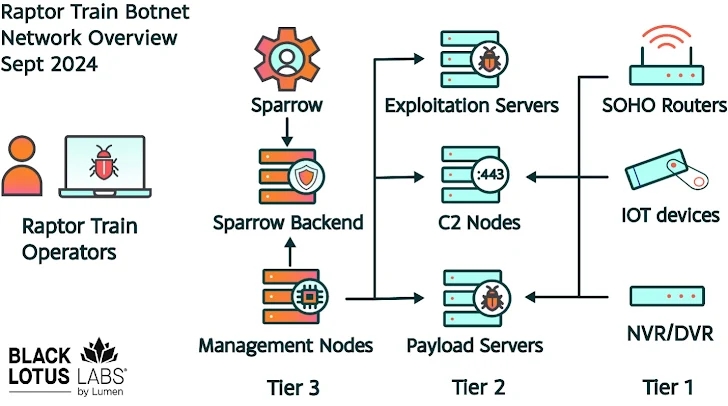
Raptor Train Operation and Infrastructure
The Raptor Train uses a three-tier network to maximize its efficiency and command and control capability:
Tier 1 (TIER 1): Includes infected devices, such as routers, IP cameras and NAS servers. Infected devices in this tier typically remain active for approximately 17 days before being replaced with new compromised devices.
The majority of TIER 1 (Level 1) nodes are geolocated in the United States, Taiwan, Vietnam, Brazil, Hong Kong and Türkiye.
Tier 2 (TIER 2): Consisting of dedicated virtual servers that act as C2 (Command and Control) servers, operating and delivering payloads to Tier 1 devices. These servers are strategically organized to make operations more difficult to detect and disturb.
Tier 2 nodes, on the other hand, rotate around every 75 days and are primarily based in the United States, Singapore, United Kingdom, Japan, and South Korea. The number of C2 nodes increased from approximately 1 to 5 between 2020 and 2022 to as many as 60 between June 2024 and August 2024.
Tier 3 (TIER 3): This tier is responsible for manually managing Tier 2 nodes and oversees botnet operations, including sending commands, collecting data, and managing exploits through a centralized interface called Sparrow . Control is exercised via SSH connections during working hours in China, suggesting that the botnet operators work regular schedules.
In total, more than 1.2 million compromised device records were identified in a MySQL database hosted on a Tier 3 management server used to administer and control the botnet and C2 servers using the application Sparrow. Sparrow also contains a module for exploiting computer networks using an arsenal of known and zero-day vulnerabilities.
Raptor Train Infection Campaigns
The Raptor Train botnet has conducted several separate campaigns since its emergence in 2020, exploiting various vulnerabilities in IoT devices and networks. These campaigns are differentiated by the C2 (Command and Control) domains and the types of devices targeted:
Crossbill (from May 2020 to April 2022): Use of the C2 domain k3121.com and its associated subdomains.
Finch (from July 2022 to June 2023): Use of the C2 domain b2047.com and its associated subdomains.
Canary (May 2023 to August 2023): Use of the C2 domain b2047.com, with a multi-stage infection.
Oriole (from June 2023 to September 2024): Use of the C2 domain w8510.com and its associated subdomains.
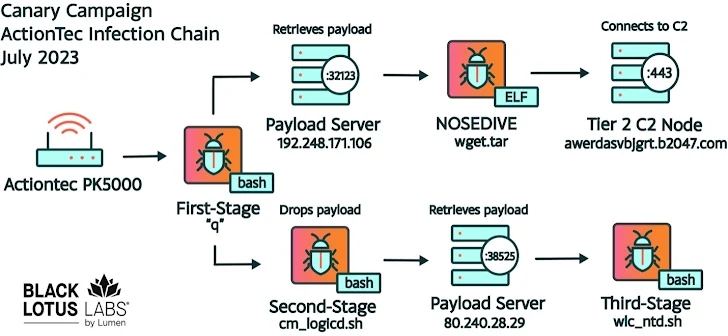
La Canary campaign focused on ActionTec PK5000 modems, Hikvision IP cameras, as well as Shenzhen TVT NVRs and ASUS routers. This campaign is notable for its use of a multi-step infection chain. The first step is to download a bash script, which connects to a level 2 payload server to retrieve malware called Nosedive, followed by a second stage bash script.
Each new stage then attempts to download and run additional scripts at regular intervals, every 60 minutes, to maintain the infection.
Exploits and Vulnerabilities Used
The Raptor Train operates over 20 different device types, including brands like TP-Link, ASUS, Hikvision, and Synology. Hackers take advantage of zero-day (unknown and unpatched) flaws and known vulnerabilities to penetrate these devices. This allows rapid propagation of the botnet, which remains resistant to traditional defense solutions thanks to the absence of persistence mechanisms in its payloads.
Impact and Targets
The botnet mainly targets strategic sectors such as critical infrastructure, telecommunications, the military sector, and higher education, particularly in the United States and Taiwan. As of June 2023, the Raptor Train already controlled 60,000 active devices, but with campaigns such as Canary and Oriole, this number has increased to over 260,000 compromised devices. The United States and other countries were also affected, with nearly 385,000 devices in the United States alone registered in the botnet's database.
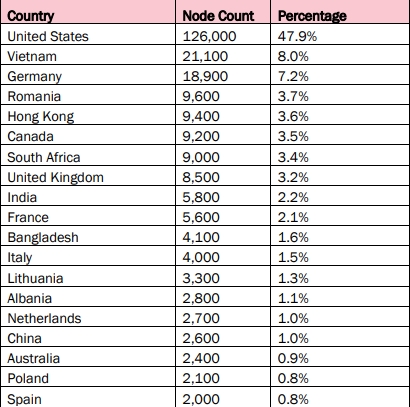
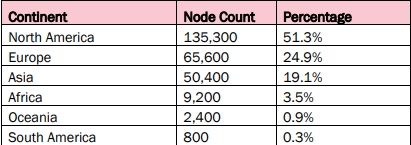
In a publication in "JOINT Cybersecurity Advisory" on September 18, 2024, the following tables were published:
“BOTNET” device by country
“BOTNET” device by continent
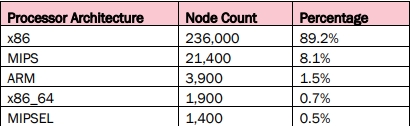
“BOTNET” device by processor architecture
Reactions and Countermeasures
Faced with the rise of Raptor Train, American authorities, with the collaboration of international organizations, carried out coordinated operations to dismantle the botnet's infrastructure. Using court orders, the FBI took control of some C2 servers and sent commands to remove malware from compromised devices. However, the botnet operators responded with an unsuccessful DDoS attack attempt against American infrastructure. The FBI and other agencies continue to monitor botnet activity, and mitigation efforts are underway to help device owners secure their networks.
Recommended mitigation measures
The FBI recommends that network defenders adopt the following actions to mitigate the threats posed by adversaries who use botnets for malicious cyber activity. These measures aim to prevent IoT devices from becoming part of a botnet, as well as protect networks already infected by botnets.
Disable unused services and ports: This includes features such as automatic configuration, remote access or file sharing protocols. Routers and IoT devices may offer features such as Universal Plug and Play (UPnP), remote management options, or file sharing services, which can be exploited by attackers to gain initial access or propagate malware. malware to other network devices. Disable these features if they are not needed.
Implement network segmentation: Ensure IoT devices are isolated into network segments to reduce risk in the event of a compromise. Use the principle of least privilege to provide devices with only the connectivity necessary to perform their function.
Monitor high network traffic volumes: DDoS attacks emanating from botnets may initially appear to be normal traffic. It is therefore crucial to define, monitor and prepare to detect any abnormal traffic. Monitoring can be done through firewalls or intrusion detection systems. Certain network solutions, such as proxies, can help mitigate DDoS incidents.
Apply patches and updates: Regularly install software updates and security patches on IoT devices. Regular patches address known vulnerabilities. If possible, use automatic update channels from trusted sources. Do not trust emails that claim to deliver software updates as attachments or links to insecure sites.
Replace default passwords with secure passwords: Many IoT products include administrative passwords in addition to other user accounts. Ensure that all passwords are changed from their default values, and enforce a strong password policy. If possible, disable password hints.
Schedule device reboots: Restarting a device terminates all running processes, which can eliminate certain types of malware, such as "fileless" malware that runs only in the host's memory . If a device is compromised, consider restarting affected devices remotely, or even manually if necessary.
Replace end-of-life equipment: Obsolete or end-of-life devices should be replaced with devices supported by vendors with regular updates and adequate technical support measures.
Conclusion
The Raptor Train remains an active threat, and although efforts have been made to disrupt its operations, its sophisticated structure and ability to exploit new vulnerabilities make it a priority target for global information security forces. Updating IoT devices and having appropriate defenses in place is crucial to limiting future infections.
Definitions of technical terms
To help better understand the technical details covered in this article, here is a series of key definitions. If you are unfamiliar with some of the concepts, this section will provide you with simple, accessible explanations of essential terms related to cyberattacks, botnets, and computer vulnerabilities. These definitions will help shed light on how the Raptor Train works and the steps the FBI is taking to dismantle this threat.
1. Botnet
Source : Kaspersky
2. DDoS (Distributed Denial of Service)
Source : Cloudflare
3. IoT (Internet of Things)
Source : IBM
4. Zero-Day Vulnerability
Source : Trend Micro
5. C2 (Command and Control)
Source : Fortinet
Sources
Last updated