Am I a victim of data leaks?

Data leak: A data leak occurs when an internal party or source exposes sensitive data, usually unintentionally or by accident. The results of a data breach can range from loss of information to malicious exploitation. Often, data leaks lead to data breaches. Source: FORTINET
Many of us have been involved in a data breach at some point in history, whether it was the big Linkedin breach of 2016 (and also 2021 for that matter) or the most recent of Facebook. It's a worrying fact of modern life: many of us, at one point or another in our online lives, will find our data caught in a hack.
If one of your online accounts has been hacked (often referred to as "pwned"), it's important not to panic. By following a few simple steps, you can check the extent of the damage and regain control of your account security.

Pwned: Refers to a person who has been beaten flatly in a video game or who has been cheated online. It has also been used to describe the act of gaining illegal access to something.
Definition: Wiktionary
Pwned, in this context, simply means that your account has been the victim of a data leak. Data leaks exist and it is one of the unfortunate side effects of the modern, internet-connected world. And often, they have nothing to do with the fact that you, a simple user without problems, are irresponsible. Businesses can experience embarrassing data breaches, whether as a result of their servers being hacked, human error, or staff misconduct. With such a number of leaks and the intensification of cyberattacks during this year of crisis, we may be led to ask ourselves the following question:
How do I know my data has been leaked?
The best-known site for checking if your email address, or any account associated with it, has been hacked is called Have I Been Pwned.
Have I been pwned ?
Have I Been Pwned? is a website that allows users to check if their personal data has been compromised by data breaches.
The main function of this site, since its launch, is to provide the general public with a way to check whether their private information has been leaked or compromised. Website visitors can enter an email address or phone number and see a list of all known data breaches with records linked to that email address. The website also provides details about each data leak, such as the history of the loss and the specific types of data it contained.
Checking my data
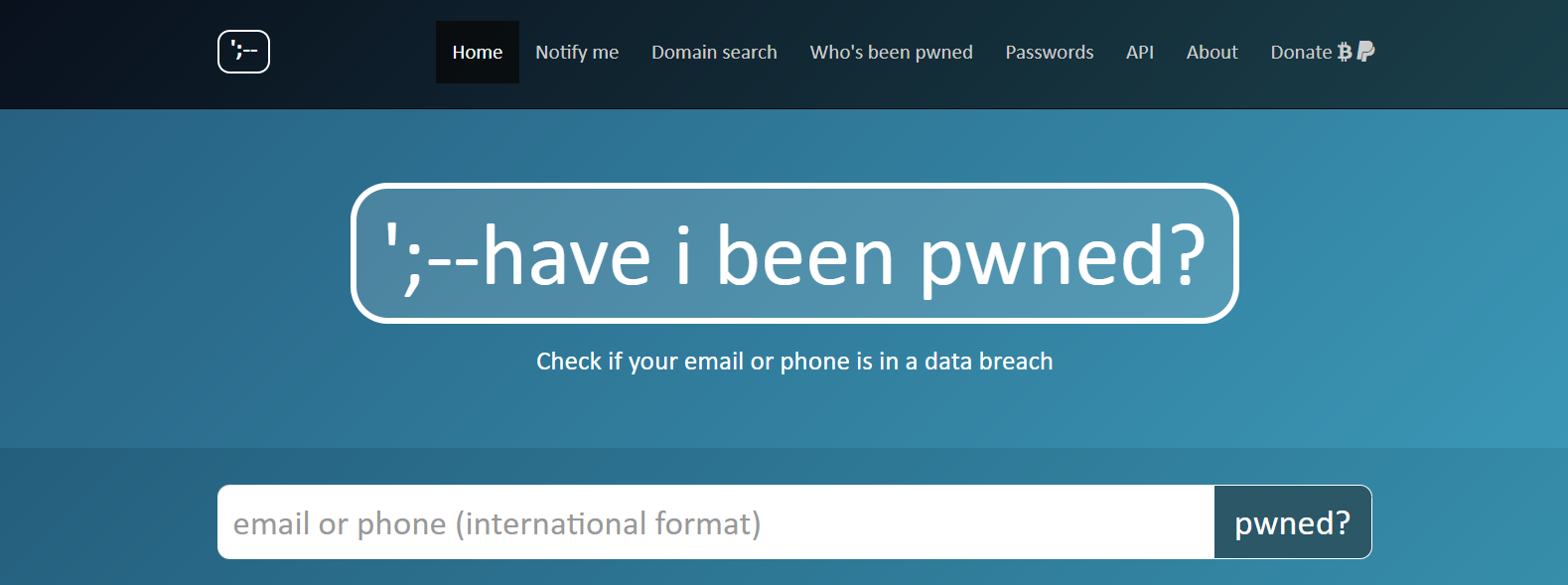
First of all, you must enter your email address (or telephone number with indicator: BE=+32, FR=+33,...) in the search bar:
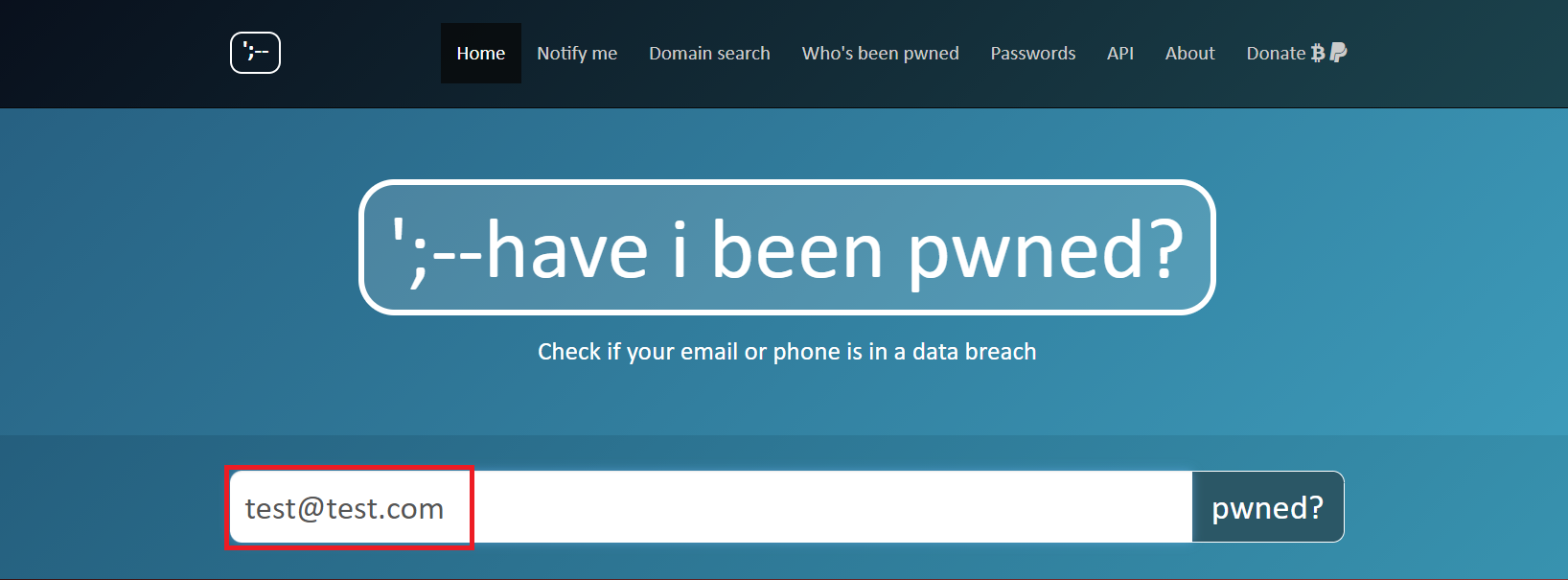
If the message "Oh no - pwned!" appears, your email address is compromised:
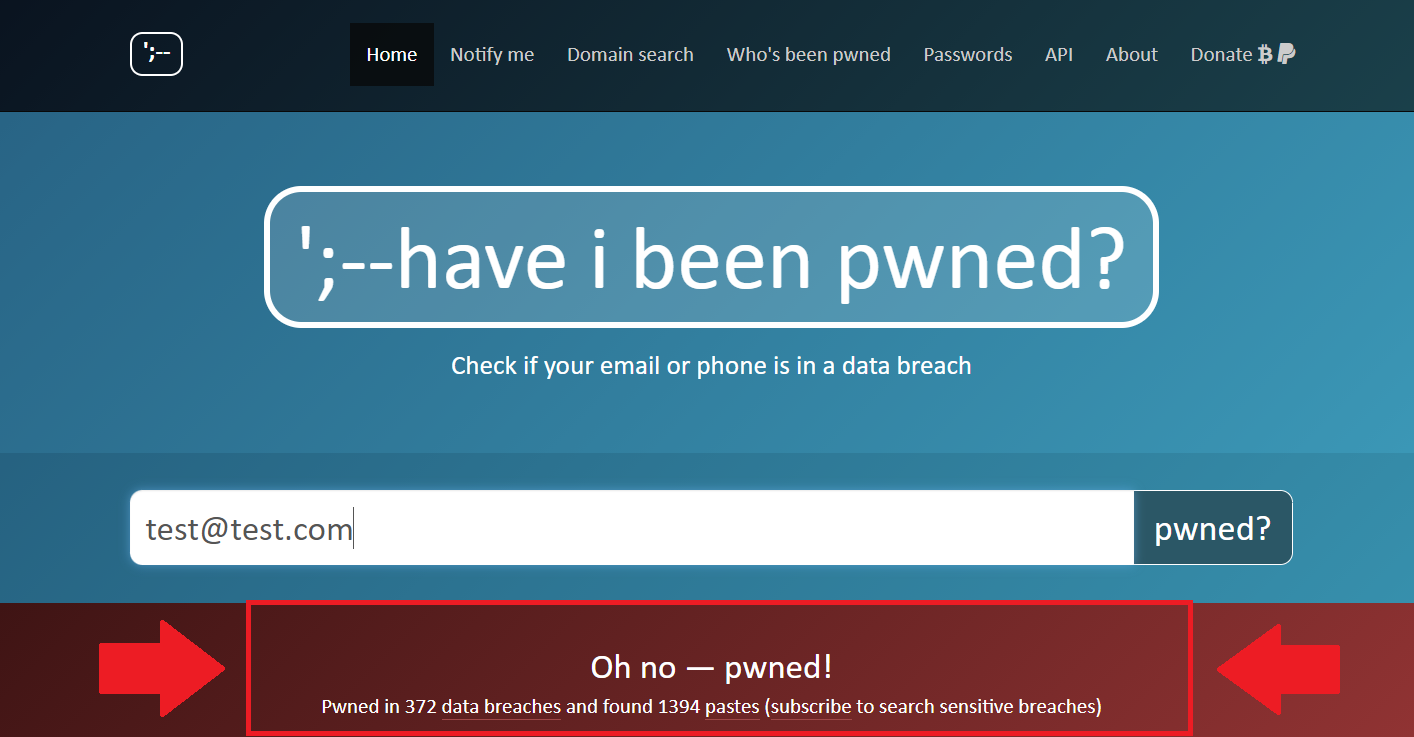
⚠ The email address "[email protected]" is present in 372 data leaks and 1394 pastes.
Paste: A "paste" is information that has been added (pasted) to a public website designed to share content, such as Pastebin.
Definition: HaveIBeenPwned?
Often, when online services are compromised, the first signs appear on "collage" sites like Pastebin. Attackers frequently post samples or complete dumps of compromised data on these services.
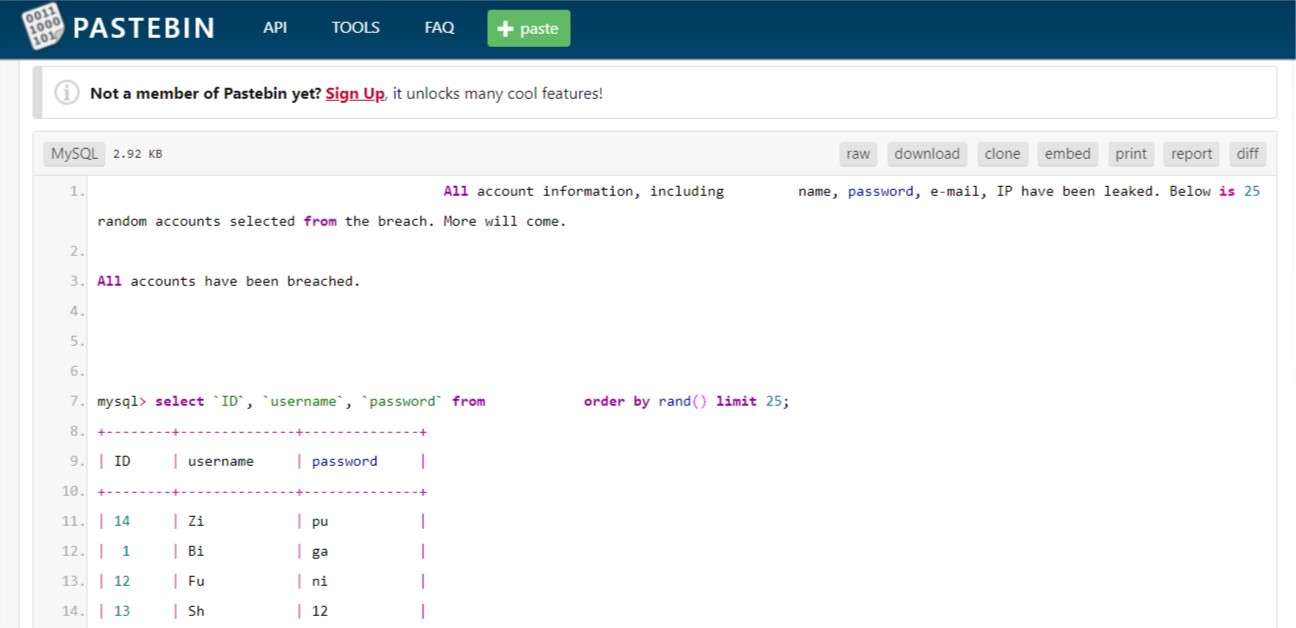
Monitoring and reporting the presence of email addresses on sites like Pastebin can give affected users a head start in mitigating the potential fallout of a data breach.
Data leaks are varied because they come from several different companies. Here are some examples:
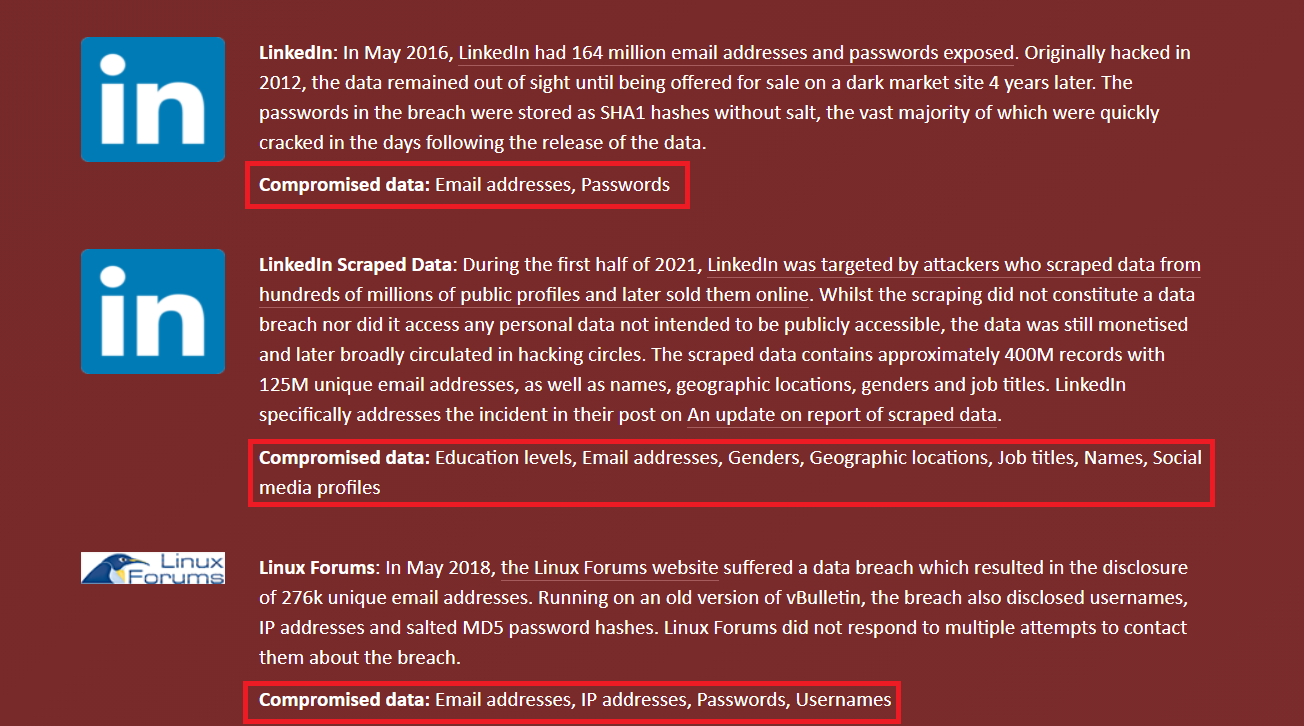
⚠ Data linked to [email protected] was leaked via Linkedin and Linux Forums (non-exhaustive list).
In the example above, the leaked data is:
Email addresses
Passwords
Education level
Geographic Location
Job title
First and last name
IP addresses
Nicknames

Indeed, if you do not have data on the internet, you do not risk any leaks. But are you sure that your email address is not linked to any account?
If, on the contrary, you have one or more accounts and some have been leaked, here is how to best react and protect yourself.
How to react and protect yourself
While it is important to know whether your personal data or identifying information has been leaked, it is even more important to act accordingly. What should you do now, knowing that your account has been compromised?
Change your passwords.
Log in to the compromised account and change the password. If a security question is enabled for password change, answer it, get a new password, and change the security question as well.
Next, update the passwords for all accounts for which you used the same login and password combination. Do not reuse passwords; be sure to choose different ones for each account.
Add double authentication.
The idea of two-factor authentication is that in addition to your password, you'll need to provide additional proof of identity, such as a passcode sent to your phone. This way, if your account is ever hacked, cybercriminals won't be able to access it using just your password.
Monitor account-related payments.
Check the appropriate accounts linked to purchasing data, shopping sites or simply your bank account, for any orders you don't remember placing. The sooner you find them, the more likely you are to cancel these orders successfully.
Inform your bank so that it can stop your card.
First call your bank, then email for proof of your report.
Check your card statement for suspicious transactions.
Also notify the bank if there are payments that you did not authorize.
Stay up to date
In order to protect yourself as much as possible from cybercrimes linked to data leaks, you must stay informed and react quickly.
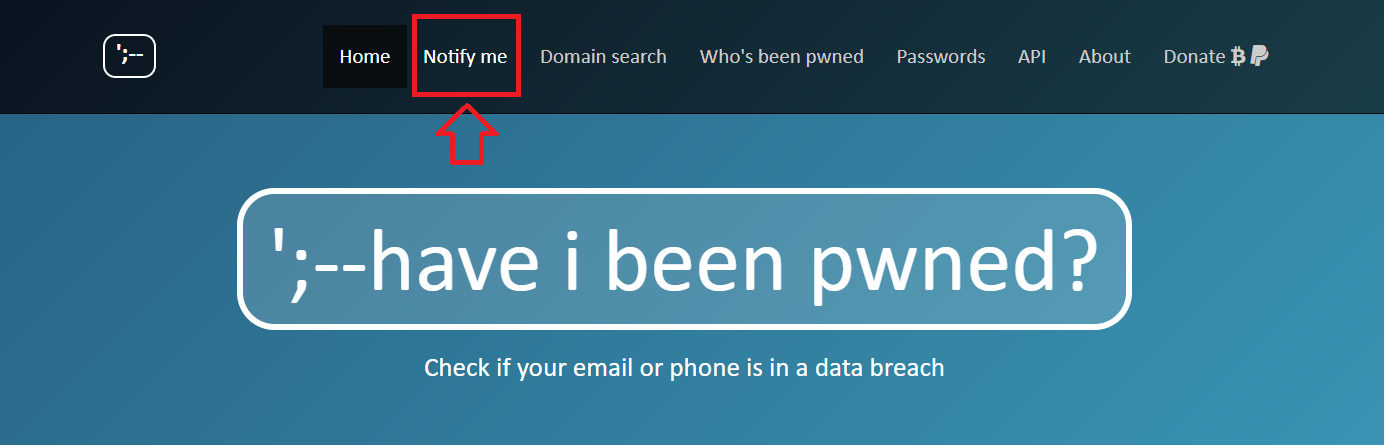
Activer la notification sur Have I been Pwned?
The primary function of Have I Been Pwned is to tell you if your information has been compromised. But other tools have been made available such as notification.
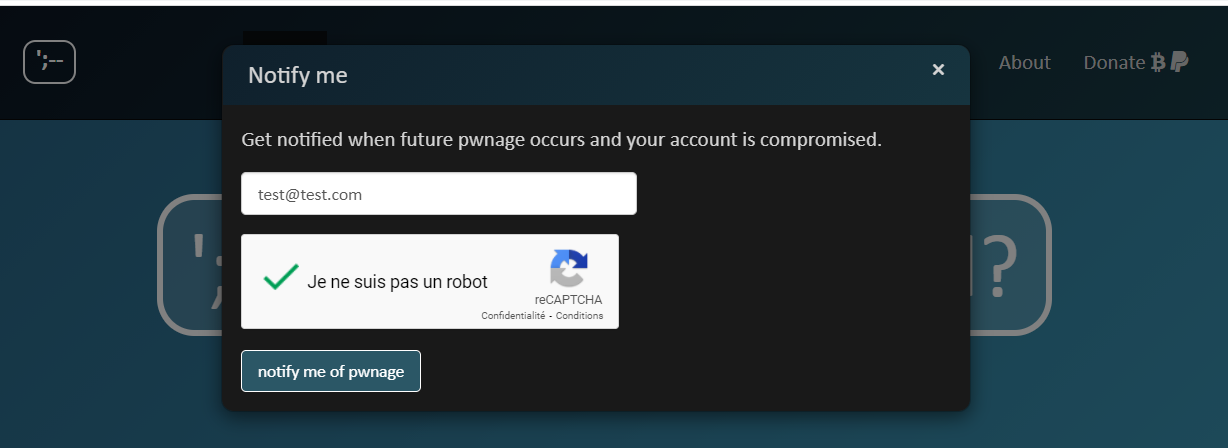
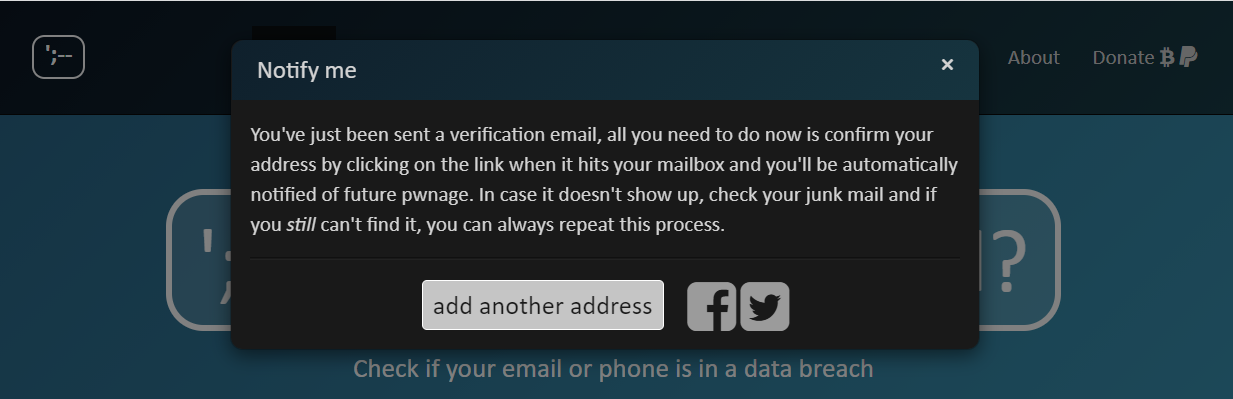
You can sign up to receive an email notification whenever your personal information is discovered in a new data breach. This will allow you to take steps to minimize the risk of fraud or identity theft, for example by changing your password for this account and any other accounts for which you have used the same password.
Check password
Password reuse is normal. It's extremely risky, yet it's so common because it's easy and people aren't aware of the potential impact.
Have I Been Pwned? has implemented a tool called "Pwned Password".
This tool contains a list of hacked passwords.
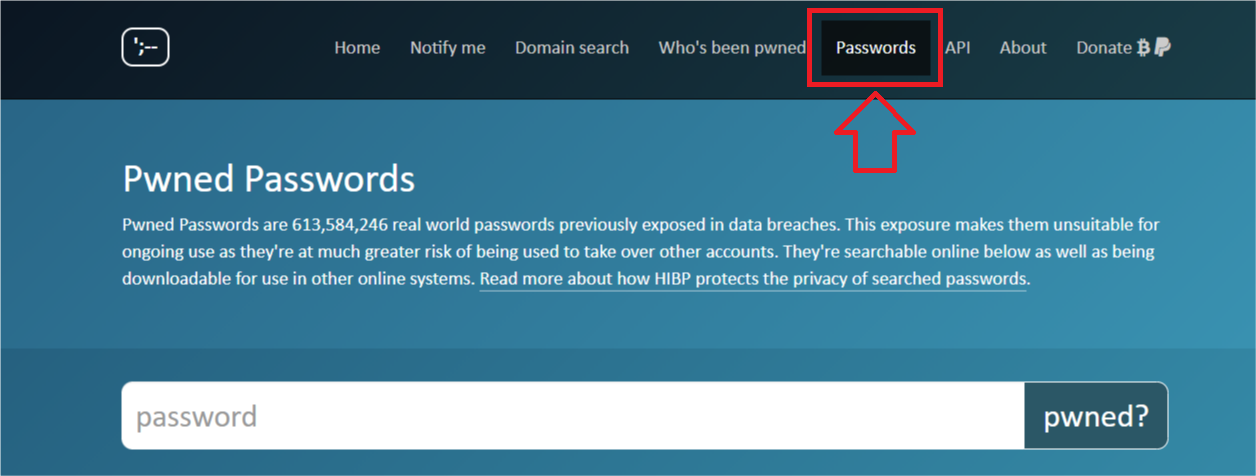
The hacked passwords are 613,584,246 real-world passwords previously exposed in data breaches. This exposure makes them unsuitable for permanent use, as they are much more likely to be used to take over other accounts.
Exemples
With the following passwords:
Test123
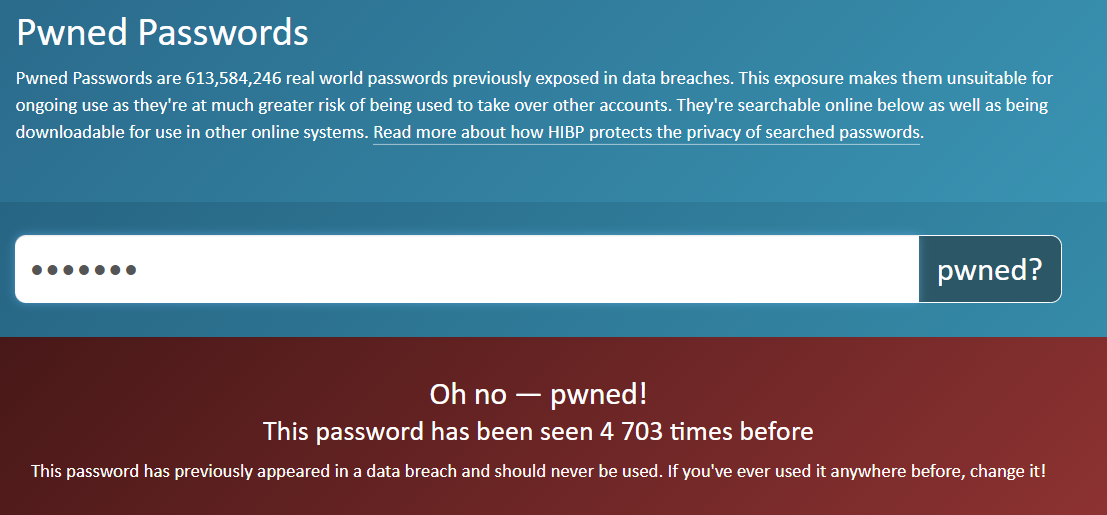
The password has been seen in data leaks 4703 times.
Ln8}fE9m-Z!s
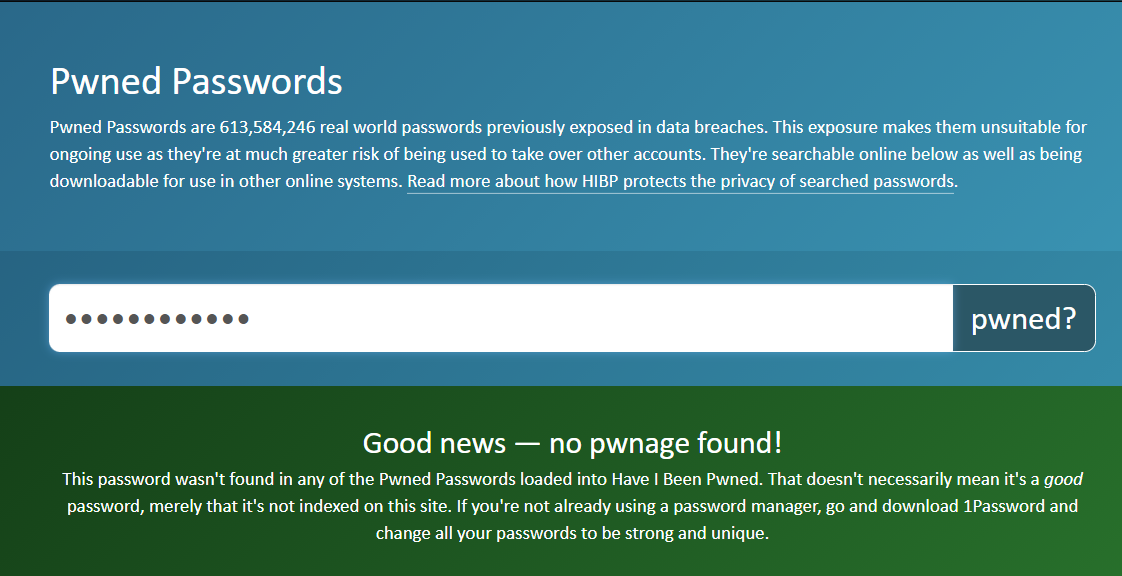
The password is not found in any known data leaks to date.
Last updated