Microsoft stresses the urgency of patching Exchange servers locally
Date: 27-01-2023
Patching et Monitoring

Microsoft today urged its customers to keep their "on-premises Exchange servers" patched by applying the latest supported Cumulative Update (CU) so that they are always ready to deploy an update emergency safety.
Patch Management: Patch management involves identifying and deploying software updates, also called “fixes” or “patches,” to various endpoints, including computers, mobile devices, and servers.
Patches are typically distributed by software developers to fix known security vulnerabilities or technical issues. They also allow you to add new features and functions to the application. These short-term solutions are intended to be used until the next version of the software is released.
Definition: Crowdstrike
Tony Redmond, le MVP de Microsoft (Most Valuable Professional), says the Exchange server update process is "simple" and recommends always running the script Exchange Server Health Checker after installing updates.
Editor's note: For the simplicity of the Windows update process, everything is relative because many system administrators could contest it with (very) good arguments.
The Exchange Server Health Checker script helps detect common configuration issues that are known to cause performance issues and other long-lasting issues that are caused by a simple configuration change in an Exchange environment. It also helps collect useful information about your server to speed up the process of collecting common information about your server.
Exchange vulnerabilities still relevant

Today's warning comes after Microsoft also asked administrators to continually patch on-premises Exchange servers after releasing emergency out-of-band security updates to fix ProxyLogon vulnerabilities that were exploited in attacks two months before the release of official patches.
As of March 2021, at least ten hacker groups were using ProxyLogon exploits for various purposes, one of them being a Chinese-sponsored threat group tracked by Microsoft under the name Hafnium.
To show the sheer number of organizations exposed to such attacks, the Netherlands Institute for Vulnerability Disclosure (DIVD) found 46,000 servers unprotected against ProxyLogon vulnerabilities a week after Microsoft security updates were released .
Most recently, in November 2022, Microsoft fixed another series of Exchange bugs known as ProxyNotShell, which allows privilege escalation and remote code execution on compromised servers, two months after the first detection of wild exploitation.
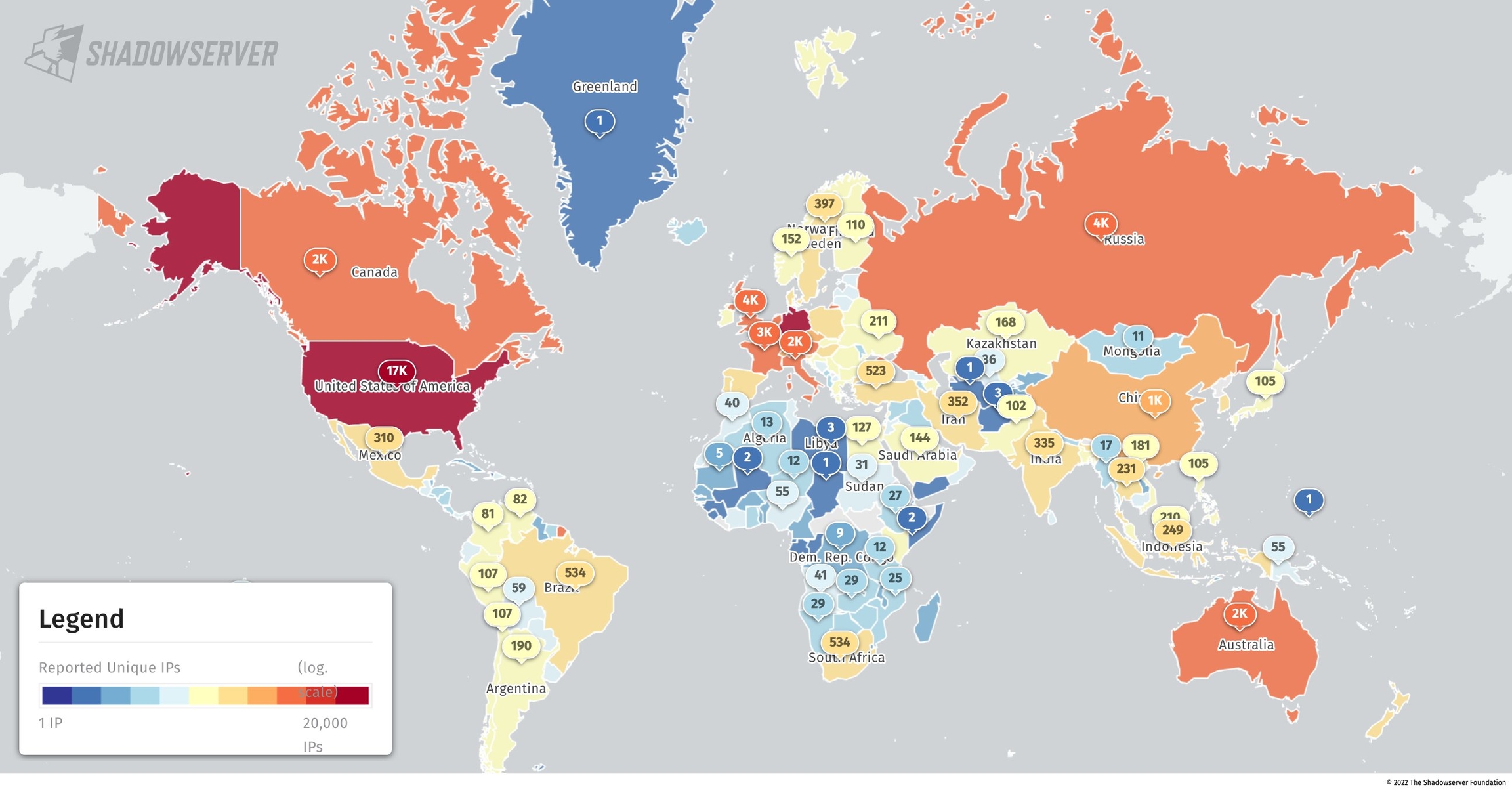
To put things into perspective, earlier this month, security researchers at the Shadowserver Foundation discovered that more than 60,000 Microsoft Exchange servers exposed online are still vulnerable to attacks leveraging ProxyNotShell exploits targeting the CVE-2022-41082 vulnerability. Remote Code Execution (RCE).
CVE:
The acronym CVE, for Common Vulnerabilities and Exposures in English, designates a public list of computer security vulnerabilities. When we talk about a CVE, we generally refer to a security vulnerability that has been assigned a CVE identifier. Security advisories published by vendors and researchers almost always mention at least one CVE identifier. CVEs help professionals coordinate their efforts to prioritize and resolve vulnerabilities, and thus strengthen the security of computer systems.
SOURCE: REDHAT
To make matters worse, a search on Shodan shows a huge number of Exchange servers exposed online, thousands of which are still waiting to be secured against attacks targeting the ProxyShell and ProxyLogon flaws, among the most exploited vulnerabilities in 2021/2022.
Shodan:
Shodan is a website specializing in the search for objects connected to the Internet, and therefore having an IP address visible on the network. It allows you to find a variety of web servers, routers as well as many peripherals such as printers or cameras. Such a request is processed with a simple analysis of the HTTP header returned by the device or server. It is then possible to retrieve lists of specific elements. For each result, we find the IP address of the server as well as other types of sensitive but accessible information. SOURCE: WIKIPEDIA
Last updated