CVE-2024-27713 - Protection mechanism Failure in Eskooly Web Product <= v3.0
Description
Eskooly web application does not use or incorrectly uses a protection mechanism that provides sufficient defense against directed attacks against the product.
Related Findings
Security Headers Misconfiguration
Technical Details
The vulnerability arises from flaws in the sign-up process that allow attackers to manipulate account settings during registration. This can lead to unauthorized privilege escalation, enabling attackers to register accounts with higher privileges than intended.
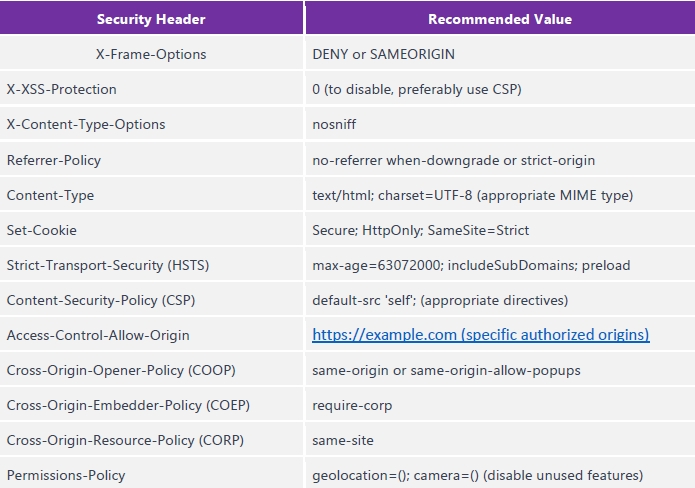
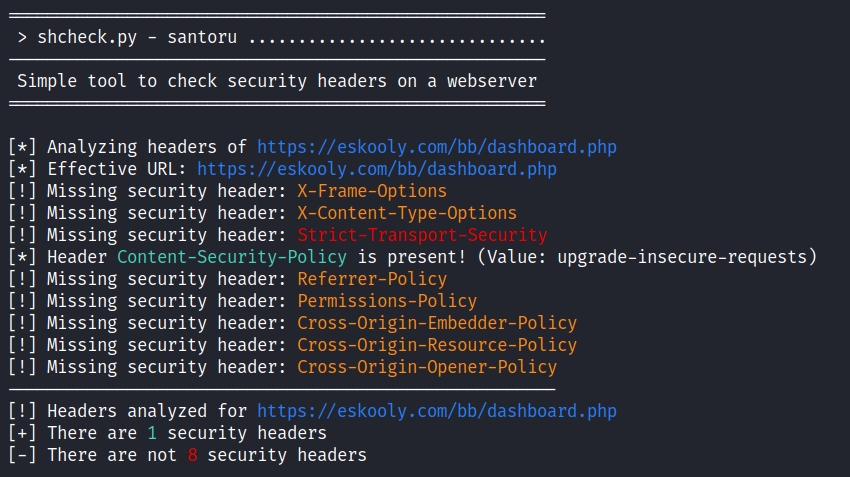
8 Security headers are missing
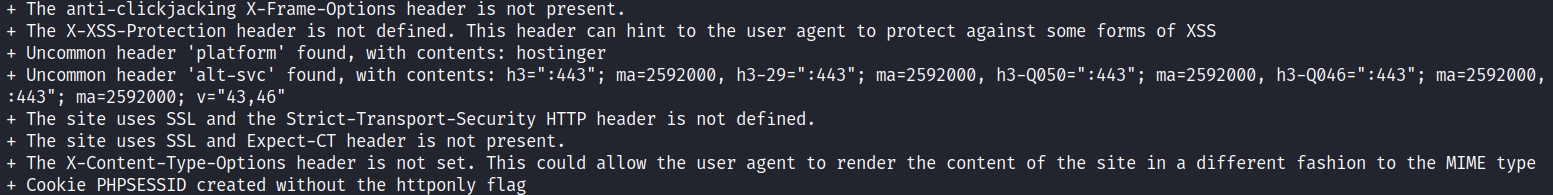
No cookie protection
Risk
Impact
Medium.
The absence of critical security headers such as X-Frame-Options, X-Content-Type-Options, Strict-Transport-Security, and others significantly increases the website's vulnerability to several types of attacks. Without X-Frame-Options, the site is susceptible to clickjacking attacks, where an attacker could trick a user into clicking on something different from what the user perceives, potentially leading to unauthorized actions. The lack of X-Content-Type-Options exposes the site to MIME type confusion attacks, where the browser might execute non-executable MIME types, leading to cross-site scripting (XSS) or other code execution attacks. Furthermore, not implementing Strict-Transport-Security can allow attackers to intercept or alter communications between the user and the website, compromising confidentiality and integrity. Each missing header contributes to an overall weakened security posture, making sensitive data and user interactions more prone to interception and manipulation.
Likelihood
High.
The likelihood of an exploit resulting from these misconfigurations is high, considering the prevalent use of automated tools and scripts that detect and exploit such vulnerabilities. The specific details of the website's traffic, user base, and content type can further influence this likelihood. High-profile or high-traffic websites are particularly attractive targets, increasing the probability of attacks. The simplicity of executing attacks like clickjacking, MIME sniffing, or SSL stripping (in the absence of HSTS) means that even less sophisticated attackers could successfully compromise the website's security. Moreover, the absence of policies like Permissions-Policy and Cross-Origin-Resource-Policy opens up additional avenues for unauthorized access and data theft, making it more likely that such vulnerabilities will be exploited if not promptly and adequately addressed.
Recommendation