CVE
Common Vulnerabilities and Exposures

Introduction
CVEs, or Common Vulnerabilities and Exposures, are unique identifiers assigned to specific software or system vulnerabilities. Their creation is intended to standardize the way vulnerabilities are referenced and shared within the cybersecurity community. The CVE initiative was launched by the MITRE Corporation in 1999 to facilitate the sharing of critical information on security flaws, enabling organizations to better protect themselves against cyber threats.
How CVEs work
CVEs are assigned by organizations called CVE Numbering Authorities (CNAs). Once a vulnerability has been identified, it is submitted to a CNA, which verifies its authenticity before assigning it a unique identifier. This process ensures that each CVE is unique, and that information is shared in a standardized way.
The CVE database, maintained by the MITRE, centralizes all registered vulnerabilities, enabling security researchers and IT professionals to consult and track known vulnerabilities. Each CVE contains a description of the vulnerability, information on the software or systems affected, and references to patches or workarounds.

Importance of CVEs
CVEs play a crucial role in security risk management. By identifying and cataloguing vulnerabilities, they enable organizations to prioritize security updates and patches. By understanding which vulnerabilities exist and how they can be exploited, companies can better protect their systems against cyber-attacks.
Security updates and patches are often triggered by CVEs. When a new vulnerability is discovered, developers work quickly to create patches which are then deployed to mitigate the risks.
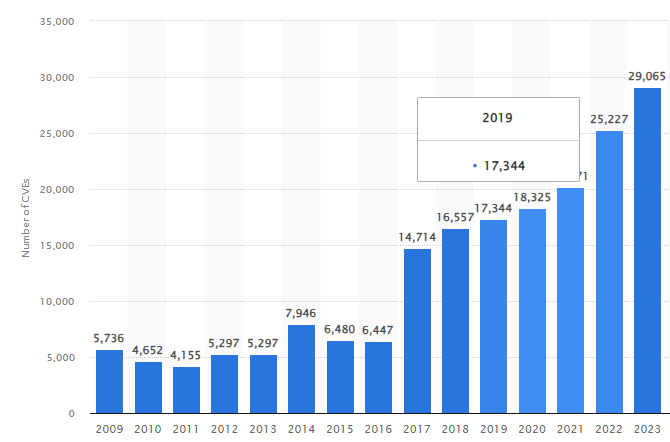
Number of CVEs between 2009 and 2023
According to a study by STATISTA 2024, the number of common computer security vulnerabilities and exposures (CVEs) is on the rise.
How to publish a CVE
Submitting a new vulnerability for assignment of a CVE follows a well-defined process. Steps include discovery of the vulnerability, full documentation of technical details, and submission to a NAC for verification. Once validated, the vulnerability receives a CVE number and is added to the database.
Just go to https://cveform.mitre.org and register your CVE, and that's it?
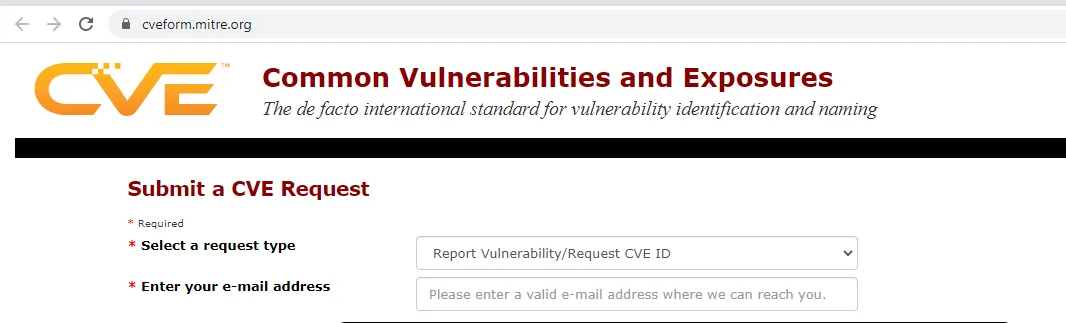
Not really. First of all, you have to fill in a certain amount of information.
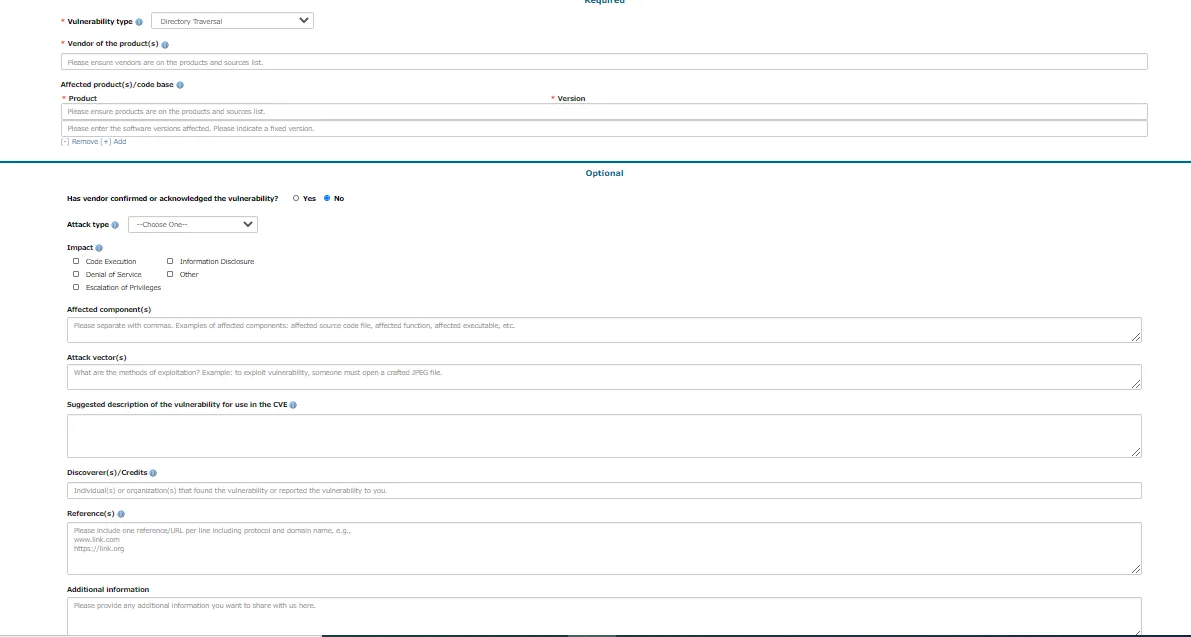
The best resource for understanding and completing the form:
After filling in the web form, we receive confirmation that the CVE(s) is/are registered and we get a number like CVE-YEAR-NUMBER (CVE-2024-XXXXX). This will not be published until a release has been sent for the vulnerability, so in the meantime you can/should contact the vendor to have the problem resolved. Publication can be carried out by the vendor if the response is present within the timeframe we've chosen, otherwise publish it ourselves:
On your blog
Via Exploit-DB
etc...
❗❗❗ ATTENTION ❗❗❗
It is VERY strongly inadvisable to publish yourself without first making several attempts to establish contact with the seller and ensure that he really understands the vulnerability.
This is an essential point, as CVEs are supposed to help improve safety, not reduce it.
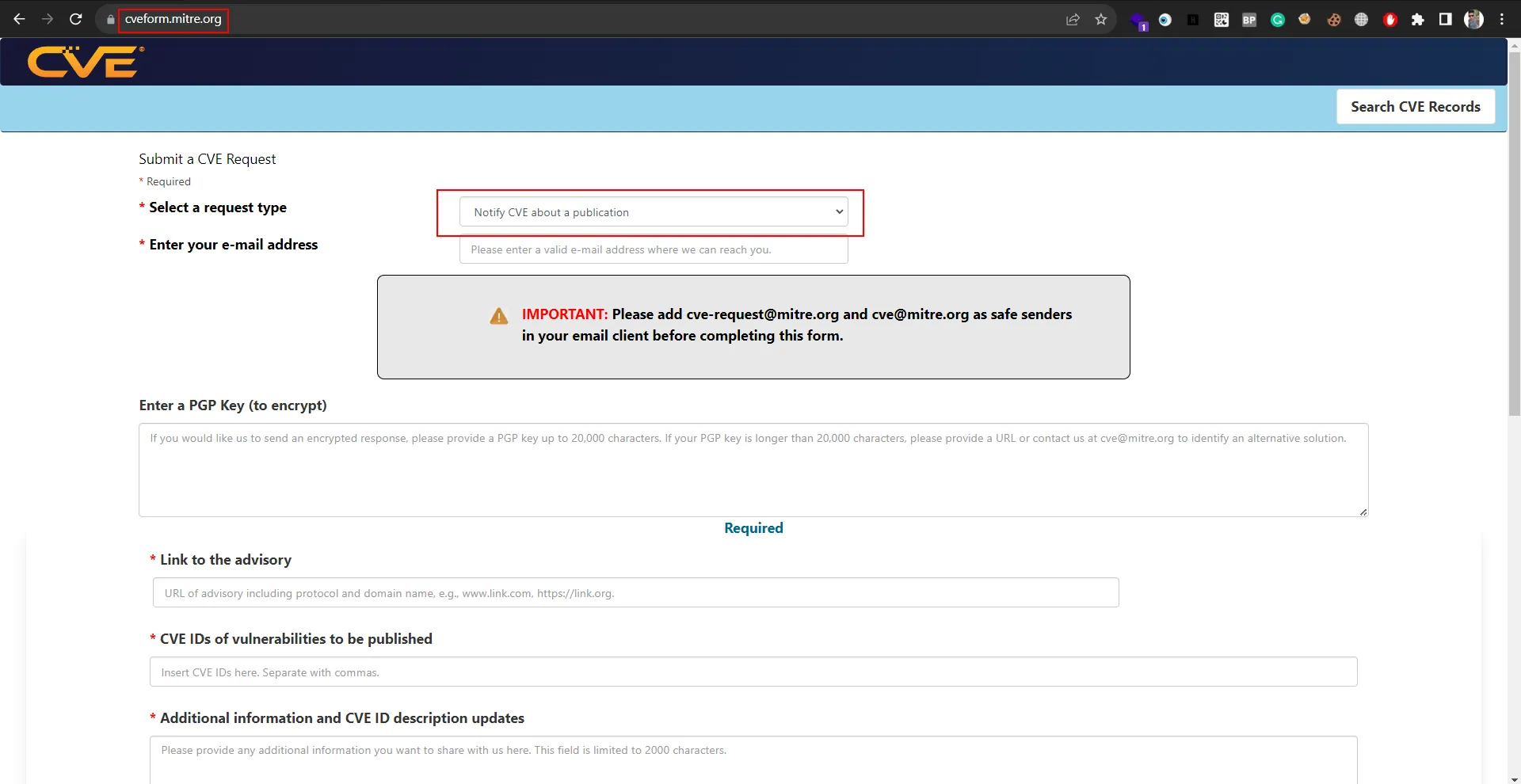
Notify CVE of your publication
Last step: Go back to https://cveform.mitre.org/, but this time select “Notify CVE About a Publication”. Share the link to your article. The CVE team verifies the publication and updates its database, consolidating your contribution.
Conclusion
CVEs are essential for maintaining the security of IT systems. By standardizing the way vulnerabilities are identified and shared, they help prevent cyber-attacks and protect sensitive data. For those wishing to expand their knowledge, there are numerous resources available to explore the subject in greater detail.
Last updated