Technology over time
Technology has evolved and will continue to evolve, with all its good and bad points.
Technological developments
Technological progress isn't the only thing increasing at an exponential rate: the speed at which newly commercialized technologies are adopted by consumers is also accelerating.
In the modern world, with increased connectivity, instant communication and infrastructure systems already in place, new ideas and products can spread at a speed never seen before, allowing a new product to reach consumers' hands in the blink of an eye.
Here's a graph showing how long it will take for the technologies mentioned to reach 50 million users (Ref: Visual Capitalist):
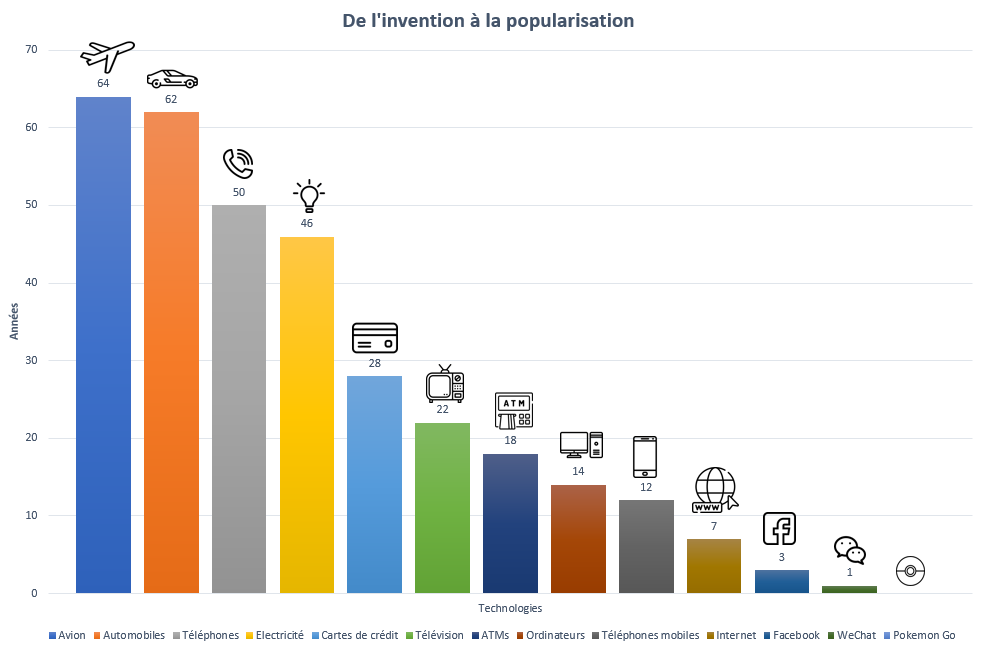
Before the advent of the Internet and digitalization, the use of a product could only spread as fast as you could manufacture the physical good. First, you needed several million dollars/francs, a factory, manpower and inventory. Then, once the product was ready for distribution, you needed mass advertising, word-of-mouth, sales channels and media coverage to have a chance.
In our graph we can see that cars took 62 years to be adopted by 50 million users. It took 28 years for credit cards to be used by 50 million people, 22 years for television, 12 for cell phones and just 19 days for Pokémon Go.
The modern era
In the modern era, therefore, there are new products that require no physical production, such as web or smartphone applications. Simply produce a useful piece of code that can be replicated or reused indefinitely at near-zero marginal cost, and it can spread like wildfire.
The applications offer a number of facilities, such as :
Access to information
The media have their own applications for conveying news
Communication
We can talk to each other by email, messenger or videoconference.
Payments
E-commerce has made online shopping easier
A European study shows that in 2019, 89% of people aged 16 to 74 in the EU had used the internet, 72% of whom had bought or ordered goods or services for private use. (Ref: Eurostat)
Applications and the Internet are part of our daily lives, whether for professional or personal reasons.
We use them to send a message to our family on a WhatsApp group, buy a gift on Amazon or send and receive e-mails on our computer, smartphone or tablet. We can therefore say that this evolution brings many positive points, as technologies can be more rapidly deployed and more easily accessible to a large number of users, but there is always a dark side:

We'll be illuminating this darkness as we travel together.
Last updated