Passwords - Protect yourself
Hackers harvest, use and sell the passwords of businesses and individuals in order to obtain financial rewards, damage reputations, steal intellectual property or carry out other illegal activities.
You must adopt good reflexes regarding passwords whether for private or professional use, here is a non-exhaustive list.
This situation is largely due to lack of employee education and corporate negligence. Within your organization, advocate for a concerted, company-wide effort on security and password protection.
11 Password Security Best Practices
1- Unique passwords for each account
Use different passwords for each account, so that if one is compromised, the others are not. This helps prevent credential-stuffing attacks, where hackers use credentials stolen from other common platforms in the hope of gaining entry.
Credential-Stuffing:
Credential stuffing is a method of cyberattack in which attackers use lists of compromised user credentials to break into a system. The attack uses bots for automation and is based on the assumption that many users reuse usernames and passwords across multiple services.
SOURCE: IMPERVA.COM
2- Characters and symbols instead of letters
Sentences using symbols such as a smiley face ":)" instead of the word "happy", or replacing the word "to" with the number "2". Using characters and symbols instead of letters can make your password more difficult for hackers or brute force attack techniques to guess.
3- Passphrases
One of the best practices for password security is to use passphrases made up of words that don't normally go together, rather than long-character passwords that are easy to forget. Passwords like "airplane puppy eating banana" are easier to remember and less likely to be hacked than "puppy running in the yard."
Use at least four words in your passphrase while respecting point 2 (Characters and symbols).
4-At least 12 characters
For optimal password security, our best practices recommend using at least twelve interchangeable characters (lowercase, uppercase, symbols, and numbers) in your password, whether or not you use a passphrase. Password length is more important for security than the use of numbers, characters, or symbols. Password length is a major indicator of how long it will take for a password to be cracked by a brute force attack or other password cracking algorithm.
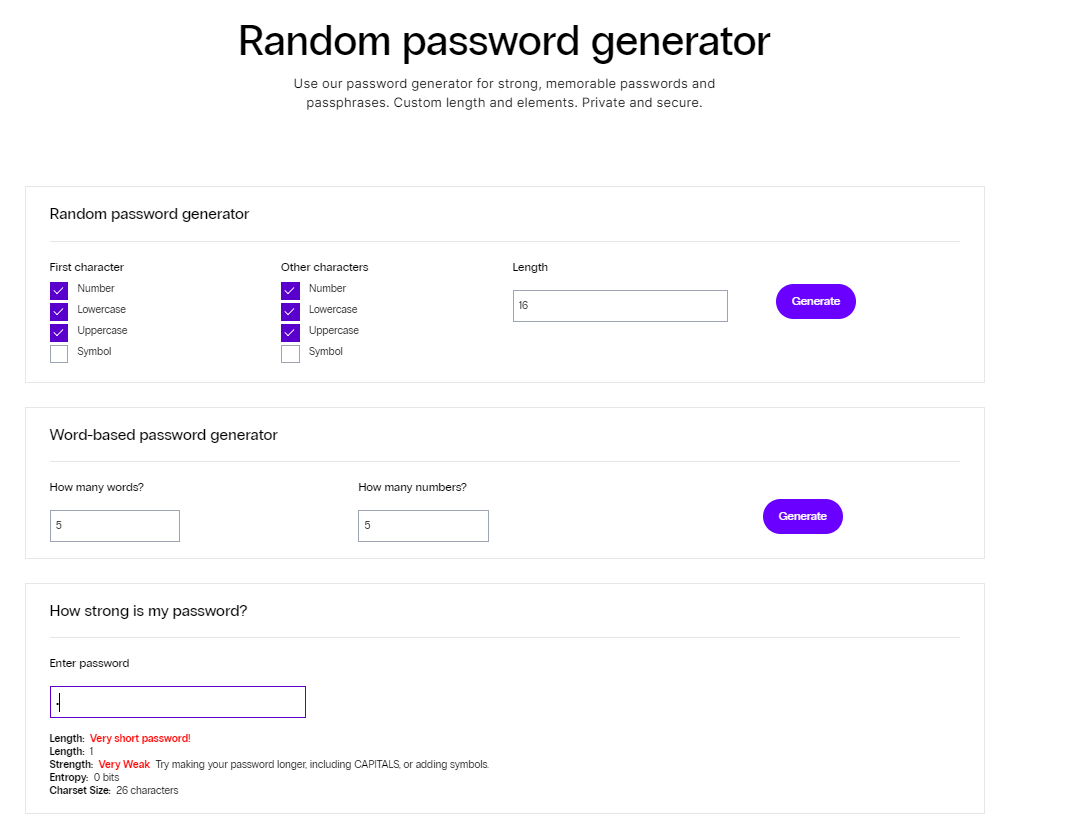
5-Analyze password strengthv
Always check the strength of your password. Most sites offer a password analyzer that shows how strong or weak your password is. Pay attention to the analyzer results and change your password accordingly to make it stronger.
Nexcess offers a unique password generation tool that allows you to create complicated passwords, generate passphrases or even check the strength of your existing passwords easily and securely, the link below below:
=> Nexcess: Random password generator
6-Change your password every quarter
Passwords can always be guessed or cracked if given enough time. This is why you should change your password every 60 to 90 days for user accounts especially in businesses. This helps ensure that hackers who use social engineering, brute force, and credential-stuffing can't use your old passwords to access your systems or data.
Obviously in practice, it is sometimes very difficult to remember all the passwords but even more complicated is the dates for changing them. In companies, there are policies automatically set up to remind and force password changes.
7-Enable two-factor authentication
Use two-factor authentication (2FA), also known as multi-factor authentication. This is a text- or app-based authentication method that verifies your identity before access. Even if a hacker somehow obtains your password, they won't be able to access your systems if they don't also have access to your phone or email, for example.
8-Use a password manager
Finally, opt for a password manager.
Password managers use multiple forms of encryption to ensure that your passwords are even harder to crack and allow you to remember only one password. Passphrases are perfect for using as the master password in your password manager, and then you can use extremely difficult passwords for your other user accounts and systems.
9- Check your credentials against data leaks
Another password security best practice is to use a security tool like Have I Been Pwned to check if your credentials have been included in recent global data breaches. This allows you to make informed decisions about which passwords should be changed immediately.
A complete article was written on our BE-HACKTIVE blog:
=> Am I a victim of data leaks?
10-Never use personal information in a password
Never use your first name, last name, age, birthday, phone number, address, bank account or other sensitive personal information in your password. Don't even use your dog's name or your favorite travel location. Most of this information is available on your Facebook account or other site/social network and therefore accessible to attackers.
11-Keep your passwords confidential
In short, don't share your passwords. This is particularly true when someone starts a conversation with you and asks you for your password, but also a loved one asks you for access to your accounts.
In general, keep your password as confidential as your banking PIN. It's that important.
Best practices for IT teams
When you are in charge of implementing password policies in your IT team, it is good to keep the following points in mind:
Limit incorrect login attempts to 5 or less
Allow passwords of 64 characters or more, rather than limiting the length to 8 or 12 characters.
Implement multi-factor authentication. Multi-factor or two-factor authentication prevents attackers from gaining access to your portals or network after cracking simple passwords.
Deploy privileged access management software for employees with access to sensitive data.
Ensure your organization uses up-to-date anti-malware and vulnerability management solutions.
Adopt the practice of changing company account passwords when an employee leaves the company.
Avoid logging in to accounts as “root” or “administrator”. Use your own login and change user (SUDO) or "runas" to execute administration commands.
Consider disabling access for "root" or "administrator" accounts.
Implement password audits. Verify that your employees are following the organization's password security policy. An audit will monitor password changes to ensure compliance. It will also highlight and correct weak access points.
Send employees reminders about password best practices. Employees generally have good intentions, but they may forget to update their passwords or comply with the organization's password policy.
Send employees email notifications reminding them of policies, best practices, and the need to rotate passwords before they expire.
Offer training sessions on password best practices.
Points de contact
Belgium
The CCB (Center for Cybersecurity Belgium) has set up an email address [email protected] to voluntarily report phishing emails.
"The goal of [email protected] is simple: we call on Internet users to voluntarily report suspicious messages they receive to this address, the famous phishing messages. We then check the URLs and annexes of these messages sent. This is an automated process. We block suspicious links. This system helps protect less vigilant Internet users who have clicked on the link.
Source: Safeonweb.be
The FPS Economy has set up a contact point for all fraud, deception, scams and scams via the following link: https://pointdecontact.belgique.be/meldpunt/fr/bienvenue
When your rights as a consumer or business have been violated or you are the victim of some form of deception, you can report it via this new site. The point of contact gives a tailor-made opinion and directs you to the appropriate body. The contact point is the result of collaboration between the Federal Agency for the Safety of the Food Chain (AFSCA), the Federal Agency for Medicines and Health Products (FAMHP), the Social Information and Research Service (SIRS), the Federal Police, the FPS Finance and the FPS Economy.
Source: Police.be
France
Cybermalveillance
The French government has set up the following site:
Cybermalveillance.gouv.fr's mission is to assist individuals, businesses, associations, communities and administrations who are victims of cybercrime, to inform them about digital threats and the means to protect themselves from them.
Last updated