Phishing - Techniques
There are a number of different techniques used to obtain personal information from users. As technology advances, so do the techniques used by cybercriminals.
To prevent phishing on the Internet, users need to know how criminals do it, and be aware of anti-phishing techniques to avoid falling victim.
This section presents the most common techniques.
Spray-and-Pray
Spray-and-Pray”, the technique by definition of phishing, consists of sending the same e-mail to as many users as possible, asking them to fill in personal data.

The most common phishing technique.
This information will be used by cybercriminals for their illegal activities. Most messages include an urgent note asking the user to enter credentials to update, modify or verify account data. Sometimes, the victim may be asked to fill in a form to access a new service via a link provided in the e-mail, such as a new Amazon, Netflix or other account.
Examples
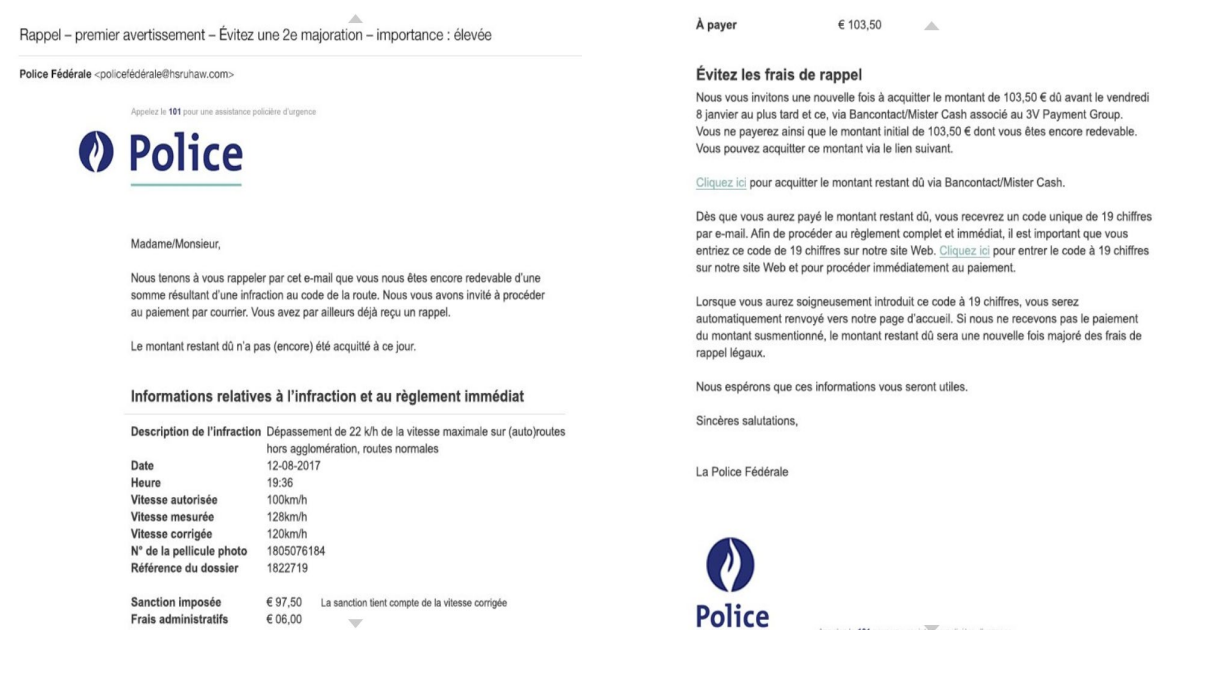
Mail from the Belgian National Police:
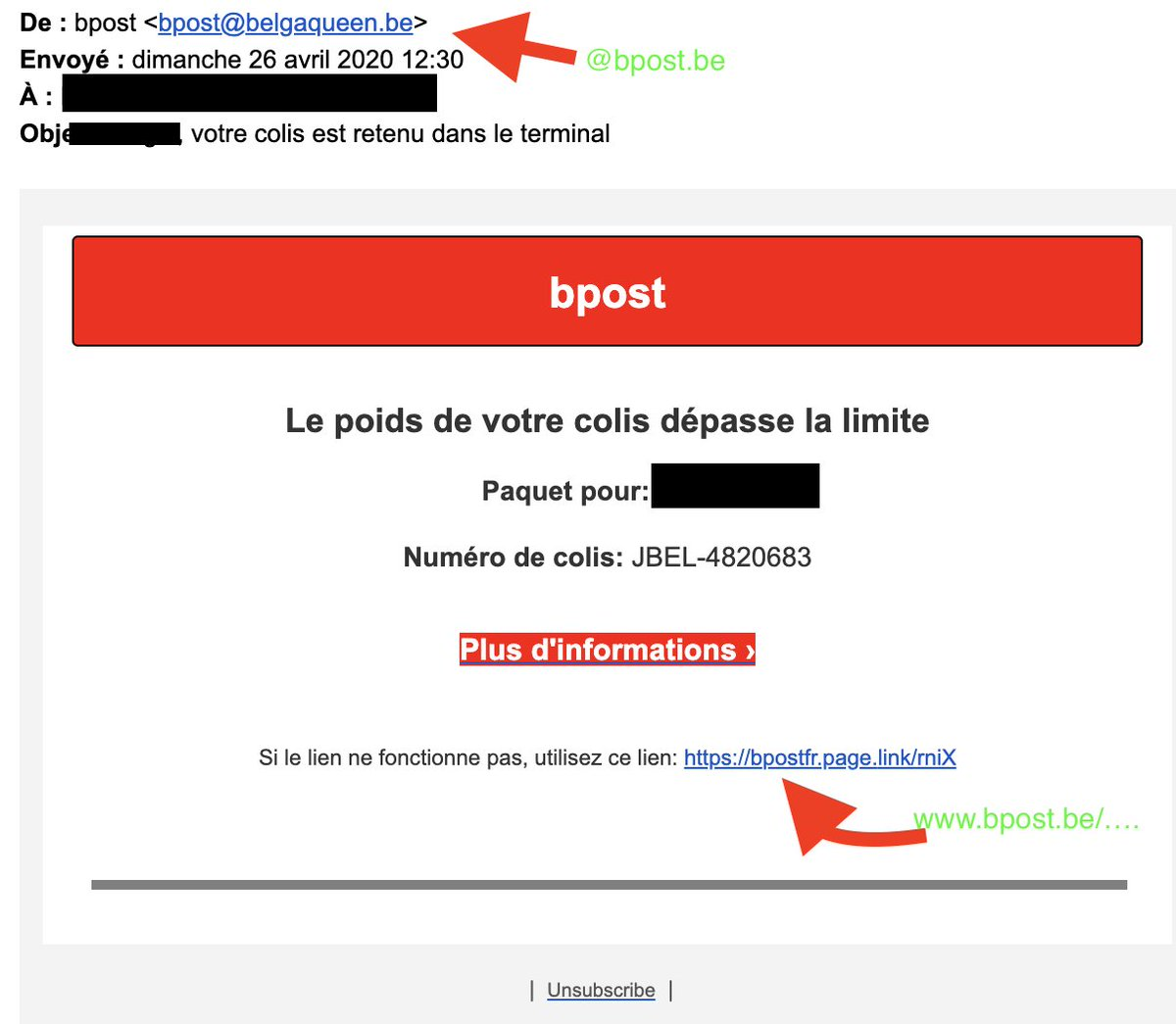
Mail from bpost:
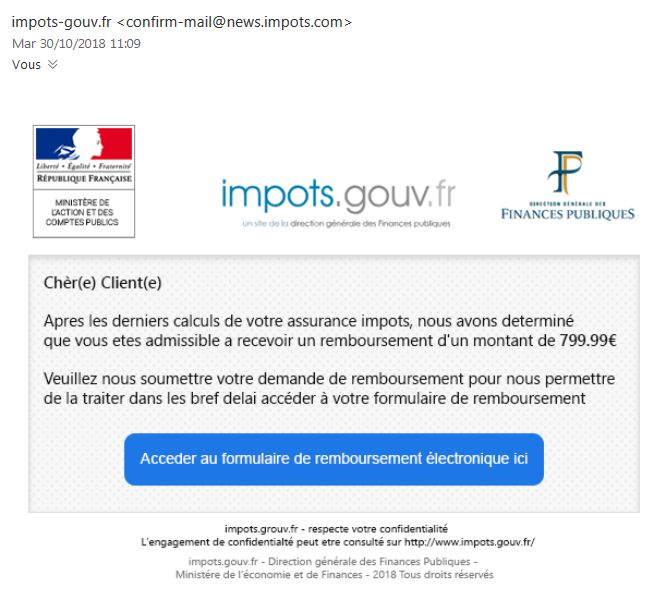
Mail from the French government:
Spear Phishing
Spear phishing” is an e-mail targeting a specific person or department within an organization, and appearing to come from a reliable source. In fact, it involves cybercriminals attempting to steal confidential information from the target in question.

Spear phishing is a highly targeted phishing method in which cybercriminals pose as a trusted source in order to convince victims to divulge confidential data, personal information or other sensitive details. The cybercriminal will then use this information for malicious purposes, including identity theft or data breaches.
Spear phishers often prey on their victims through targeted emails, social media, direct messaging apps, and other online platforms. The strength of these cyberattacks lies in the fact that they are tailor-made for the victims and that they favor quality over quantity unlike phishing (spray-and-pray).
Examples
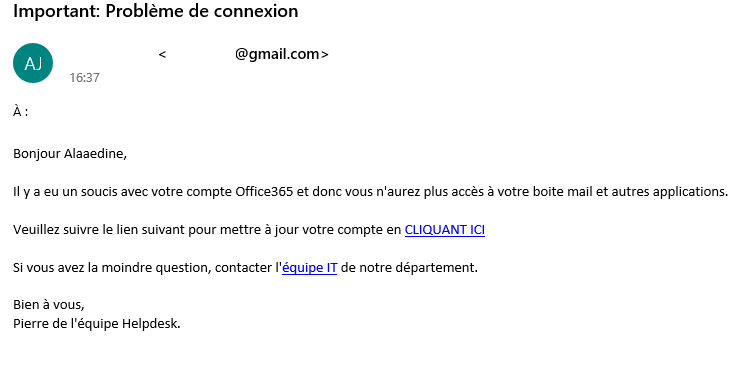
Mail personnel:
Phishing via search engines
“Search engine phishing” occurs through online website search engines. The person may find offers or messages there that encourage them to visit the website. The search process may be legitimate, but the website is actually fake and exists only to steal the person's personal information.

Some phishing scams involve search engines where the user is directed to sites that may offer products or services at low prices for example. When the user tries to purchase the product by entering their credit card details, these are collected by the phishing site. There are many fake banking sites that offer users cheap credit cards or loans, but they are actually scam sites.
Examples
Here are some of the common tricks used by sites to lure victims:
Great Discount/Free Offer
These sites appear to be typical online retailers, but the products are fake and if you order something, you will never receive it. Instead, online fraudsters will take your money and probably your identity too.
Low interest rate/free credit card
Be wary of banking institutions offering incredibly low rates. These are likely fake sites designed to trick you into signing up or even transferring money from other sources.
Job offer
An online job search can turn up fake offers from companies that don't exist. The application will ask for personal information, for example a National Insurance number or bank details. No company should need this information before hiring you.
Emergency Warnings
Some sites use emergency warnings to encourage customers to download their products. Pop-ups tell you that your computer has been infected with malware or that your antivirus subscription has expired.
Pop-up: De l'anglais "to pup up" qui signifie surgir. Une pop-up parfois appelée fenêtre intruder, pop-up window or advertising window, is a secondary window which is displayed, without having been requested by the user, in front of the main navigation window when browsing the Internet. (Definition: Wikipedia)
wishing
“Vishing” comes from two English words: Voice and phishing. This is a phishing technique that requires making a phone call.

Vishing involves convincing victims that they are doing the right thing by responding to the caller. Often the person calling claims that it is a call from the government, the tax office, the police or the victim's bank.
Examples
Telemarketing
These cybercriminals pretend to be calling from a legitimate company like one you are already a customer of or a company that offers deals you can't resist. For example:
A travel agency that offers you free vacations, all expenses paid.
A lottery that calls you to tell you that you have won a prize, even if you have never entered the contest.
Government fraud
In this type of voice phishing attack, scammers pretend to belong to a government agency such as the Federal Public Service Finance (FPS Finance) or the police. They play on your fear and sense of urgency, telling you that you owe them money and need to pay them back immediately. Otherwise, you will be fined or worse.
Fix a problem with your account
A caller who claims to be from your bank or another organization you do business with, explains that there is a problem with access to your account, a payment you recently made, suspicious transactions or perhaps be a refund owed to you. The caller asks for information, such as your passcode or account number, to resolve the problem.
Smishing
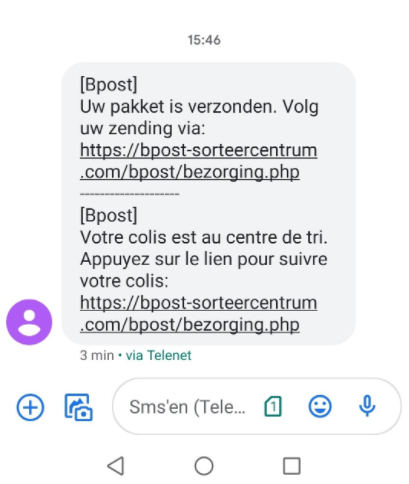
“Smishing” comes from SMS and phishing. It is a fraudulent practice of sending text messages pretending to be from reputable companies in order to trick people into revealing personal information, such as passwords or credit card numbers.
Phishing carried out via SMS (Short Message Service), a telephone text messaging service.
Deception and fraud are essential elements of any SMS phishing attack. As the cybercriminal adopts an identity that you could trust, you are more likely to succumb to their demands.
Examples
SMS from bpost:
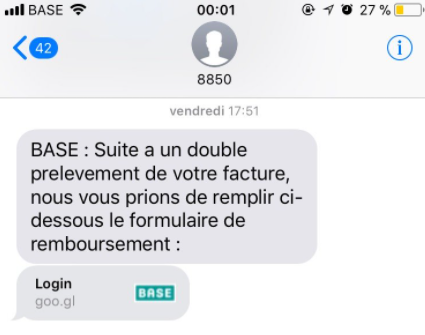
SMS from BASE:
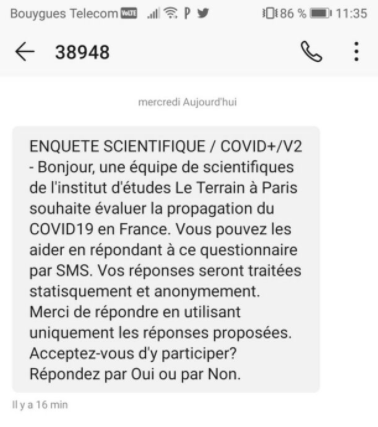
SMS for a COVID study in France:
Last updated