Malware - Evolution
Since Creeper to date, several malware have emerged.
In this section, a brief overview of the history and evolution of malware over time.
This list is of course not exhaustive, there are so many different malwares!
A summary of malware can be found HERE
Years: 1970 - 1999
1975 - ANIMAL
A program called ANIMAL, released in 1975, is generally considered the world's first example of a "TROJAN HORSE" attack.
When ANIMAL is run, it asks twenty questions for clues and attempts to guess an animal the user is thinking of. ANIMAL searches for directories that the current user has access to. If the directory does not contain an up-to-date version of Animal, it will copy itself to this directory. It will overwrite any older version of Animal, but will take care not to remove other programs.
ANIMAL creator John Walker dropped the program in San Francisco, and after about a week he was in Washington DC.
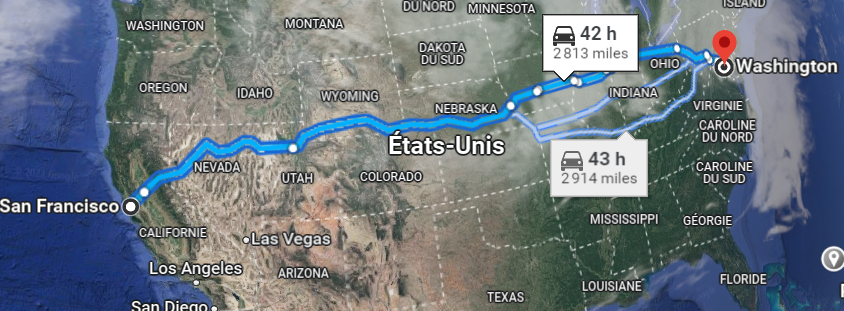
It is unlikely that Animal caused any measurable damage. The program did not contain any deliberately malicious code and did not even exploit any system vulnerabilities. It even took care not to affect any of the user's programs.
1982 - ELK CLONE
The widespread use of Apple II computers predetermined the fate of this machine by attracting the attention of virus writers. It is not surprising that the first large-scale computer virus outbreak in history occurred on the Apple II platform.
Elk Cloner was created by Rich Skrenta as a prank in 1982. Skrenta already had a reputation as a prankster among his friends because, while sharing computer games and software, he would often modify floppy disks so that they would turn off or display mocking messages on the screen.
Elk Cloner spread by infecting the Apple II operating system, stored on floppy disks. When the computer was booted from an infected floppy disk, a copy of the virus would automatically boot. The virus did not normally affect computer operation except to monitor disk access. If an uninfected floppy disk was accessed, the virus copied itself onto the floppy disk and infected it as well, slowly spreading from floppy disk to floppy disk.
Elk Cloner virus has infected the boot sector of Apple II computers. At the time, operating systems were stored on floppy disks: the floppy disks were therefore infected and the virus was launched each time the machine was started. Users were surprised by the side effects and often infected their friends by sharing their floppy disks, because most people had no idea what viruses were, much less how they spread.
The Elk Cloner virus included rotating images, flashing text, and humorous messages in poem form:
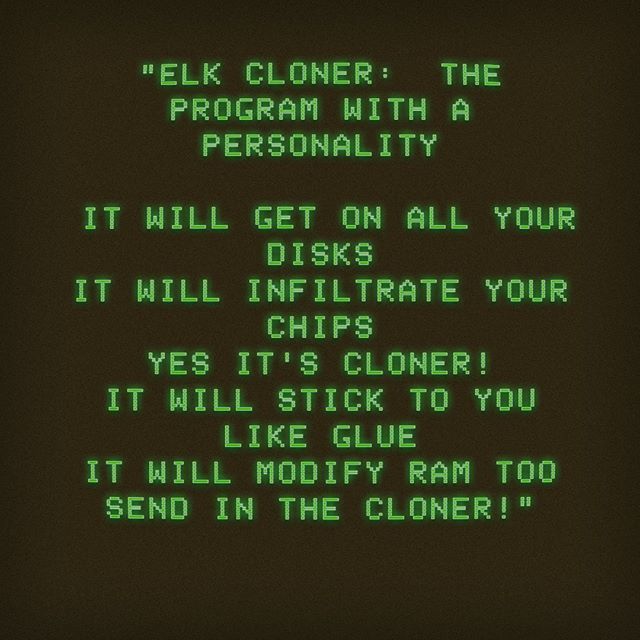
The message read:
ELK CLONER (Definition: Someone who creates clones):
THE PROGRAM WITH A PERSONALITY
IT WILL INSTALL ON ALL YOUR DISKS
IT WILL GET INTO YOUR CHIPS
YES IT’S A CLONE!
IT WILL STICK TO YOU LIKE GLUE
IT WILL ALSO MODIFY THE RAM
SEND HIM CLONE!
1983 - VIRUS
In 1983, the term "virus" was first coined by Frederick Cohen (also known as Fred Cohen) and his colleague Leonard Adleman (also known as Len Adleman) to describe self-replicating programs.
Frederick Cohen, a graduate student at the University of Southern California, provides a glimpse of the digital future by demonstrating a computer virus during a security seminar at Lehigh University in Pennsylvania.
Cohen inserted his validation code into a Unix command and, five minutes after running it on a mainframe, he took control of the system. In four other demonstrations, the code managed to take control in an average of half an hour, bypassing all security mechanisms in effect at the time. It was Cohen's academic advisor, Len Adleman (the A in RSA encryption), who compared the self-replicating program to a virus, thus coining the term.
It defines a "virus" as "a program that can 'infect' other programs by modifying them to include a possibly evolved copy of itself."
1986 - Brain
BBRAIN is considered the first PC virus (IBM Personal Computer) and was the cause of the first PC virus outbreak. Written by two brothers from Lahore, Pakistan Amjat Farooq Alvi and Basit Farooq Alvi, Brain hit the startup industries, spread widely across the world, and ushered in the modern era of viruses in computing. The perpetrators deny, and continue to deny, any malicious intent, claiming that they only targeted people who had themselves violated the brothers' copyrights in their proprietary medical software.
Brain would move the boot sector and mark it as bad, replacing the original boot sector with his own code. It spread itself when a new floppy disk was inserted into an infected machine and displayed a message that even contained the contact details of the authors:
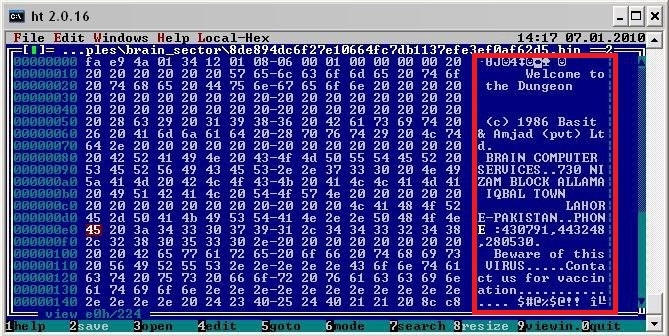
The full message was:
Welcome to the Dungeon © 1986 Basit & Amjad (pvt) Ltd. BRAIN COMPUTER SERVICES 730 NIZAB BLOCK ALLAMA IQBAL TOWN LAHORE-PAKISTAN PHONE:430791,443248,280530. Beware of this VIRUS…. Contact us for vaccination…………!!
And in French:
Welcome to the Dungeon © 1986 Basit & Amjad (pvt) Ltd. BRAIN COMPUTER SERVICES 730 NIZAB BLOCK ALLAMA IQBAL TOWN LAHORE-PAKISTAN PHONE:430791,443248,280530. Beware of this VIRUS.... Contact us for vaccination............!!
The message indicates the names of the authors, the address and the telephone number to contact them.
1992 - Michelangelo
On March 6, 1992, a virus from before the Internet era caused what was arguably the first public malware scare in history.
Michelangelo is classified as a boot sector virus, a type of virus that infects the boot sectors of storage devices, usually the boot sector of a floppy disk or the MBR (Master Boot Record) of a hard drive .
Master Boot Record:
The Master Boot Record (MBR) is the first sector of a hard drive (and previously floppy disks), which contains information to identify the location and status of an operating system in order to to boot (load) it into the computer's main memory or random access memory (RAM). The Master Boot Record is sometimes called a "partition sector" or "master partition table" because it includes a table that locates each partition in which the hard drive was formatted.
Definition: WHATIS.Techtarget
Boot sector viruses are primarily spread through physical media such as floppy disks or USB sticks. They typically infect computers that boot using disks containing the malware, activating each time the storage device is loaded.

In Michelangelo's case, once the virus infects a computer, it remains inactive until a specific date, March 6 of each year, to be exact. On March 6, any computer infected with Michelangelo had critical data on its startup disk overwritten, damaging the disk and rendering it unusable and the data almost unrecoverable.
There is no reference to the artist in the virus, and it is doubtful whether the developer(s) of the virus intended to establish a link between the virus and the artist who was born on March 6, 1475. The name was chosen by researchers who noticed the coincidence of the activation date. The actual significance of this date for the author is unknown. Michelangelo is a variant of the Stoned virus, already endemic in 1987.
Michelangelo's authorship has never been discovered. Given the times and lack of financial demands, Virus was likely written for the author's pleasure rather than possible financial gain.
At its peak, the Michelangelo virus gained notoriety for its supposed large-scale impact. Antivirus pioneer John McAfee estimated that the malware could have infected up to 5 million computers, which was a considerable number in the early 1990s. Major media outlets of the time picked up the story and made it a major news story - a devastating security incident that could have wreaked havoc on computers around the world. Needless to say, the news caught public attention at a time when malware awareness was still low.
On March 6, 1992, Michelangelo's impact was different than expected. Only a few thousand computers were found to have been infected by the virus, which was far from the highest estimates. In fact, research after the alert found that other virus variants were being discovered far more frequently than Michelangelo.
Years: 2000 to 2017
2000 - ILOVEYOU
ILOVEYOU, sometimes called LoveLetter or LoveBug, is a computer worm that attacked more than ten million Windows personal computers beginning on May 5, 2000.
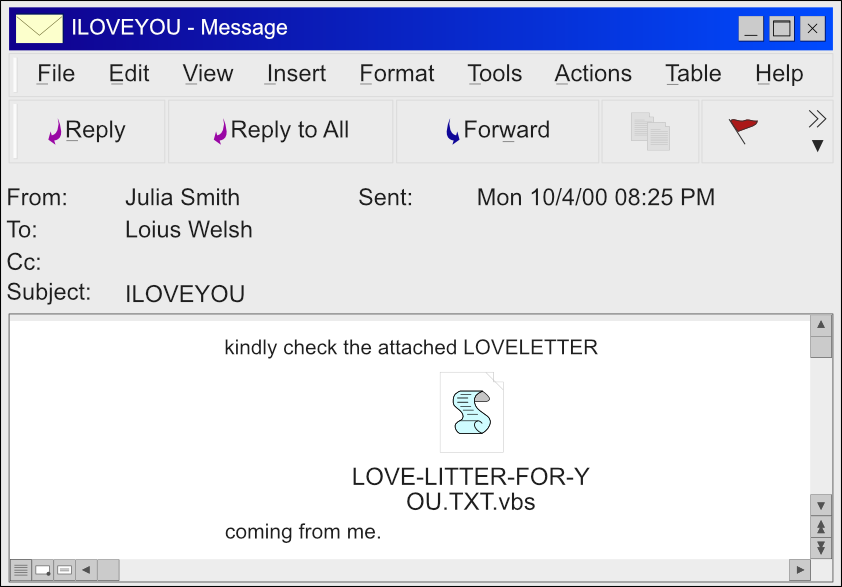
Identifiable by its attachment "LOVE-LETTER-FOR-YOU" and its subject line "ILOVEYOU", ILOVEYOU was one of the first worms to attract media attention. It is also one of the first to reach a multibillion-dollar damage toll, making it one of the most dangerous viruses.
This program was written by two young Filipino computer programmers, Reonel Ramones and Onel de Guzman, students at the AMA Computer University in Makati, Philippines.
He said the worm was very easy to create, thanks to a Windows 95 bug that executed code in email attachments when the user clicked on them. Originally designed to work only in Manila, it removed this geographic restriction out of curiosity, allowing the worm to spread worldwide. De Guzman did not expect this global spread.
2003 - SQL Slammer Worm
The SQL slammer worm is a computer virus (technically, a computer worm) that caused a denial of service on some Internet hosts and significantly slowed general Internet traffic, starting at 05:30 UTC on January 25, 2003.
It spread quickly, infecting most of its 75,000 victims within 10 minutes. Although titled "SQL slammer worm", the program did not use the SQL language; it exploited two buffer overflow bugs in Microsoft's flagship SQL Server database product. Other names include W32.SQLExp.Worm, DDOS.SQLP1434.A, the Sapphire worm, SQL_HEL, and W32 /SQLSlammer.
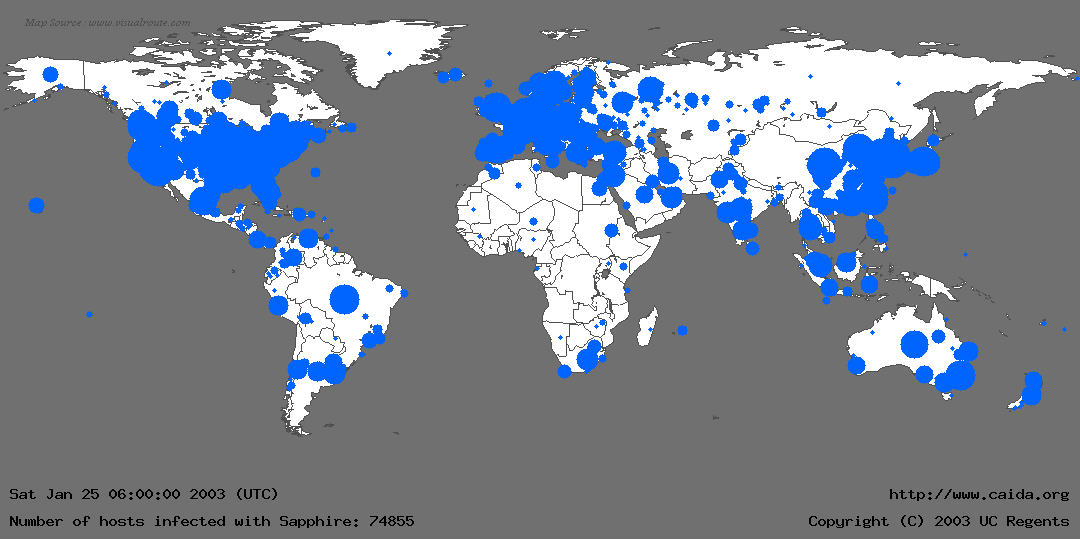
According to members of NSF, DARPA, Silicon Defense, Cisco Systems, AT&T, NIST and ACAA, SQL SLAMMER's propagation strategy relies on random scans: it selects IP addresses at chance to infect them and eventually finds all the susceptible hosts.
Random scan worms initially spread exponentially, but rapidly infecting new hosts becomes less efficient because the worm spends more effort retrying addresses that are either already infected or immune.
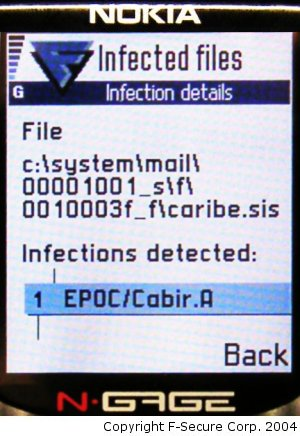
2004 - Cabir Virus
Exactly ten years ago, we discovered the first real virus written for smartphones of the time (Nokia N-Gage, for example). It was called Cabir and it opened up a whole new world for malware analysts, virus writers and ordinary users. Here are some facts about this decade-old malware:
The malware was named Cabir due to its resemblance to the "Caribe" character string found in the virus body and in honor of Kaspersky Lab employee Elena Kabirova, who accidentally entered the anti-malware lab during the discussion about the name.
Cabir spread among the most popular smartphones of 2004 - Nokia devices based on Symbian.
The only infection channel was Bluetooth. It was very easy to become infected while commuting, at a restaurant, at a concert or sporting event. One of the largest Cabir infections was detected during the Athletics World Cup held in Helsinki.
To protect a smartphone from Cabir, you had to deactivate Bluetooth or simply put it in “invisible” mode.
Kaspersky Lab analysts deliberately searched for two Nokia smartphones to study malware in the wild - this type of device was considered expensive in 2004. Since then, Kaspersky Lab has systematically purchased all the most popular models of mobile devices in order to search for malware for a given platform.
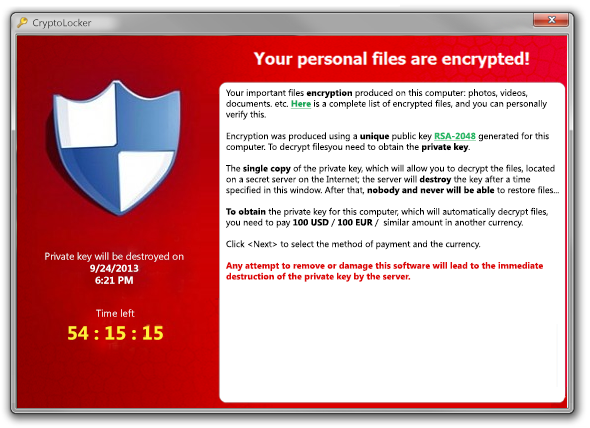
2013 - Cryptolocker ransomware attack
The CryptoLocker ransomware attack was a cyberattack using CryptoLocker ransomware that occurred from September 5, 2013 to late May 2014.
Ransomware:
Ransomware is a type of malware that prevents or limits users' access to their system, either by locking the system screen or locking users' files until a ransom is paid. More modern ransomware families, collectively known as cryptoransomware, encrypt certain types of files on infected systems and force users to pay the ransom through certain online payment methods to obtain a decryption key. Definition: TREND MICRO
A complete chapter will be developed on ransomware.
The attack used a Trojan targeting computers running Microsoft Windows and is believed to have first appeared on the Internet on September 5, 2013.
Trojan horse:
A Trojan horse is a type of malware, which should not be confused with viruses or other parasites. Trojan is software that appears legitimate, but contains malicious functionality. Its aim is to bring this malicious feature into the computer and install it without the user's knowledge.
Definition: WIKIPEDIA
It was spread through infected email attachments and an existing Gameover ZeuS botnet. When activated, the malware encrypts certain types of files stored on local drives and mounted network drives using RSA public key cryptography, with the private key only stored on the file's controlling servers. program.
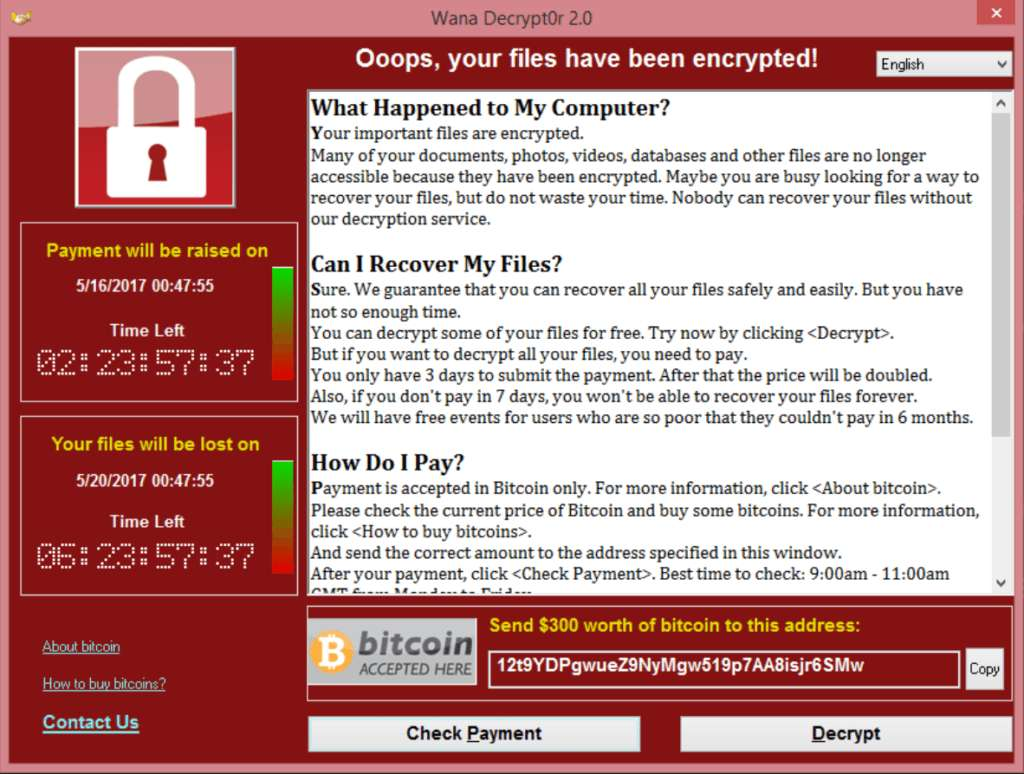
2017 – WannaCry Ransomware
The WannaCry ransomware attack is a global cyberattack carried out in May 2017 by the WannaCry ransomware cryptoworm, which targeted computers running the Microsoft Windows operating system by encrypting data and demanding ransom payment in crypto -Bitcoin currency.
EternalBlue was stolen and leaked by a group called The Shadow Brokers a month before the attack.
ETERNALBLUE:
EternalBlue is both the name given to a series of Microsoft software vulnerabilities and to the exploit created by the NSA as a cyberattack tool. Although the EternalBlue exploit – officially named MS17-010 by Microsoft – only affects Windows operating systems, anything that uses the Server Message Block version 1 (SMBv1) file sharing protocol is technically at risk of being the exploit. target of ransomware and other cyberattacks.
Definition: Wikipedia
Exploit or exploit code:
An exploit or exploit code is, in the field of computer security, a program element allowing an individual or malicious software to exploit a computer security vulnerability in a computer system.
While Microsoft had previously released patches to close the exploit, much of WannaCry's spread came from organizations that had not applied those patches or were using old, end-of-life Windows systems.
These fixes were imperative to enterprise cybersecurity, but many were not implemented due to ignorance of their importance. Some cited the need for 24/7 operation, aversion to the risk of previously working applications breaking due to patch changes, lack of staff or time for install, or other reasons.
Last updated