Intercept HTTP traffic with Burp Proxy
Burp Proxy allows you to intercept HTTP requests and responses sent between Burp's browser and the target server. This allows you to study how the website behaves when you perform different actions.
But how does a proxy work?

How does a proxy work?
Definition
A proxy is essentially an intermediary between your computer (or whatever device you use to access the Internet) and the website or service you are trying to access. When you use a proxy, your Internet request is sent first to the proxy server, then it sends it to the Internet on your behalf and receives the response, which is then forwarded to your device. This can provide privacy and security benefits because the website or service does not directly see your device, but rather the proxy server.
Plan
To visualize the process, here is a simple diagram:
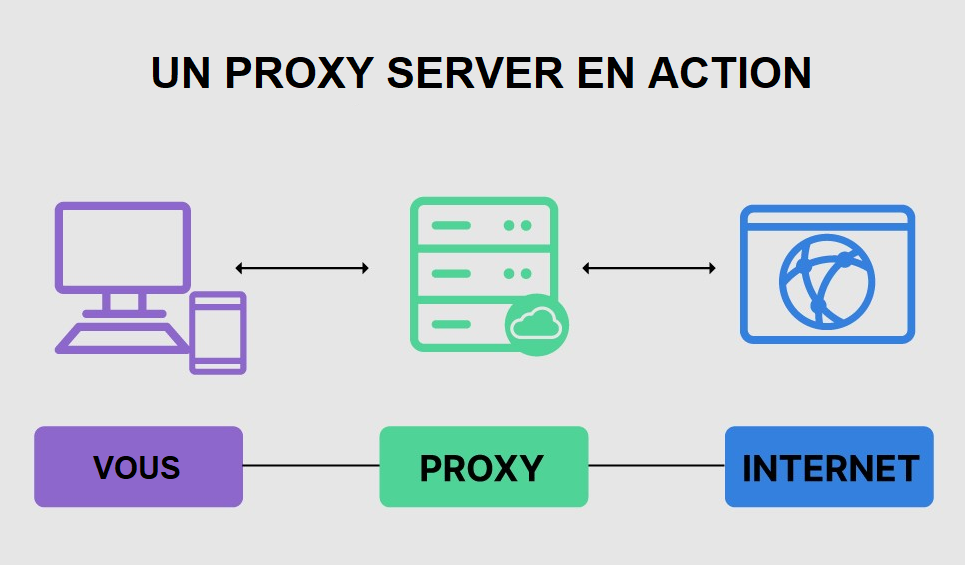
Because a proxy server has its own IP address, it acts as an intermediary between a computer and the Internet. Your computer knows this address, and when you send a request over the Internet, it is routed to the proxy, which then receives the response from the web server and transmits the page data to your computer's browser, such as Chrome , Safari, Firefox or Microsoft Edge.
Examples of use
Anonymity: Proxies can hide your real IP address, making it difficult for websites to track your online activity.
Security: Proxies can filter incoming traffic to block potential threats before they reach your device.
Bypassing geographic restrictions: For example, if certain content is only available to users in a certain region, you can use a proxy located in that region to access it.
Types de proxy
There are different types of proxies, some examples of which are:
HTTP Proxy: These are the most common types of proxies used for web traffic. They can help hide your online identity and access blocked websites.
SOCKS Proxy: Unlike HTTP proxies, SOCKS proxies can handle any type of traffic, not just web traffic. They are therefore more versatile, but also slower.
Transparent Proxies: These proxies do not hide the user's IP address and are often used for content caching and large-scale networking.
Anonymous proxies: These proxies hide your IP address, but they tell websites that they are a proxy. They offer a certain level of anonymity, but not as much as so-called “elite” proxies.
Elite Proxies: These proxies hide both your IP address and the fact that they are a proxy. They offer the highest level of anonymity.
The actual uses of these proxy types vary. For example, an HTTP proxy can be used for anonymous web surfing, while a SOCKS proxy can be used for torrenting. Transparent proxies are often used by enterprises for content caching and load balancing, while anonymous and elite proxies can be used for activities requiring a high level of privacy and anonymity.
Proxy HTTP avec BURP
Browser via BURP
Burp Proxy allows you to intercept HTTP requests and responses sent between Burp's browser and the target server. This allows you to study how the website behaves when you perform different actions.
Launch Burp Browser:
Go to the Proxy > Interception tab.
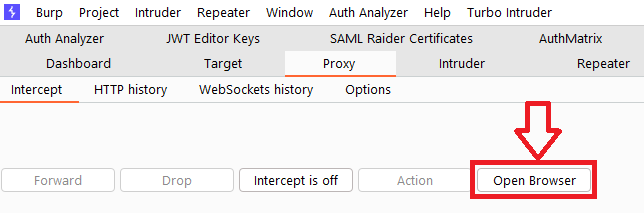
This launches the Burp browser, which is preconfigured to work with Burp directly:

Manual configuration
It is possible to configure your Browser so that it can intercept requests without using the default BURP Browser.
Addon: FoxyProxy
An Addon allows you to facilitate configuration. It exists on Firefox and Google Chrome.
Configure the Addon
Open addon option
2) Add your configuration
Nom: Burp Proxy
Type de Proxy: HTTP
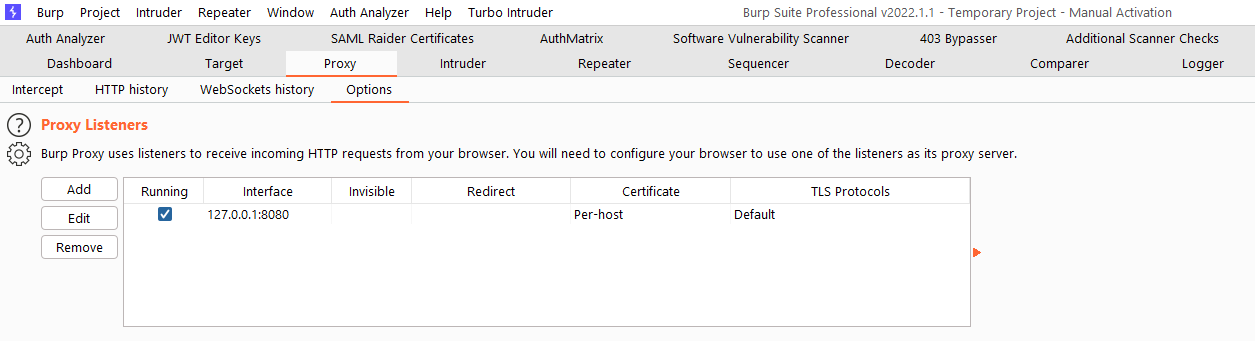
IP address: 127.0.0.1 (which you can find in the BURP options)
Port: 8080 by default (you can change it also in BURP options)
To safeguard
3) Result:
Intercept an HTTP request
Intercept
Click the “Intercept is off” button so that it changes to “Intercept is on”.
Using Burp's browser or your browser with the FoxyProxy addon, try visiting a site (example: google.com) and observe that the site does not load.
The Burp proxy intercepted the HTTP request issued by the browser before it could reach the server. You can see this intercepted request in the Proxy > Intercept tab.
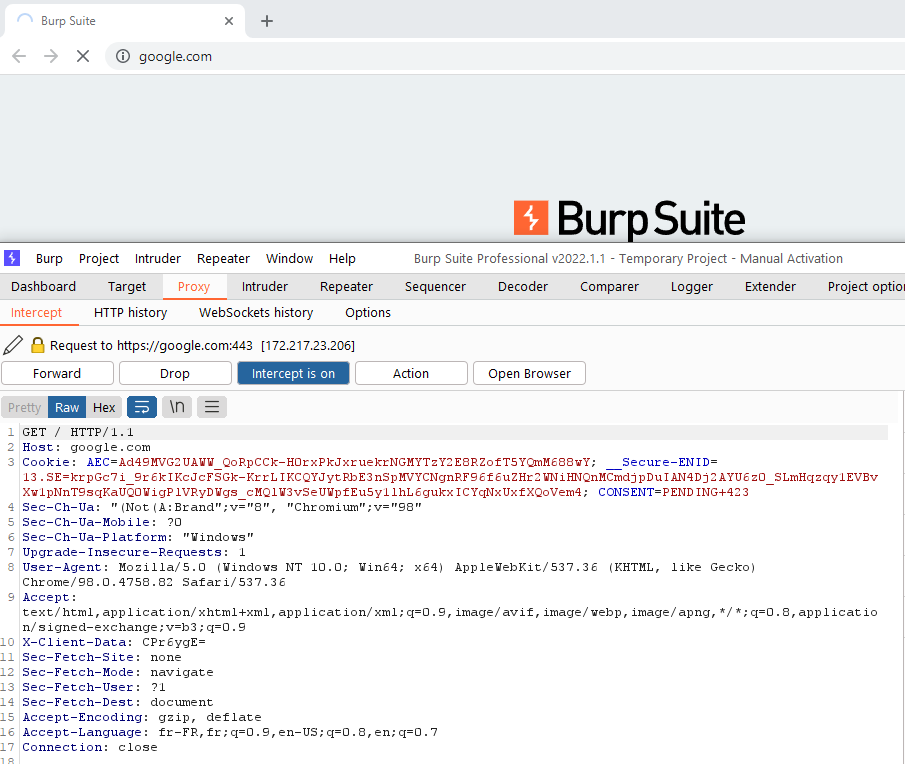
The request is kept here so that you can study it, or even modify it, before transmitting it to the target server.
Forward the request
Click the "FORWARD" button several times to send the intercepted request, and all subsequent ones, until the page loads in Burp's browser.
Disable interception
Due to the number of requests that browsers typically send, you often won't want to intercept every single one. Click the “Intercept is on” button to turn interception off.
To test that requests are no longer intercepted, return to the browser and confirm that you can now interact with the site as usual.
View HTTP history
In Burp, go to the Proxy tab > HTTP History. There you can see the history of all HTTP traffic that passed through the Burp proxy, even when interception was disabled.
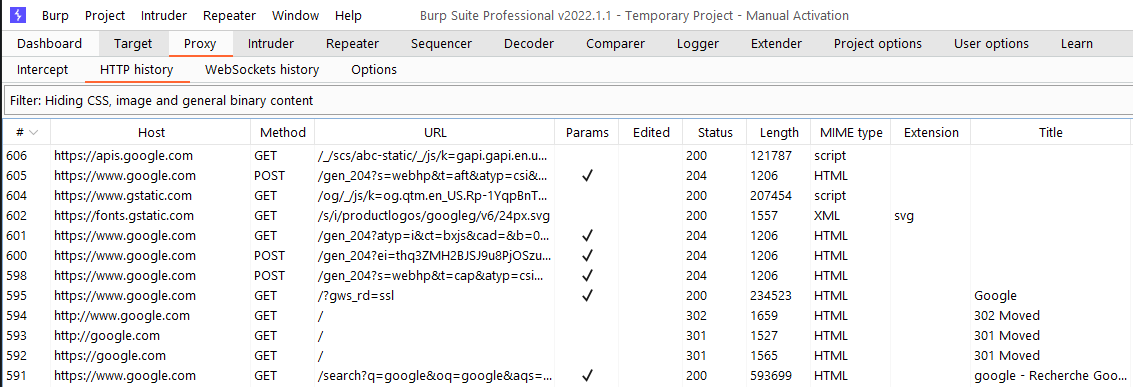
Click any history entry to view the raw HTTP request, along with the corresponding server response.
Last updated