Malware - Categories
In this chapter, I will introduce you to the most common categories of malware. This list is obviously exhaustive.
Category table
Types
Functionality
Exemple Réel
Ransomware
Ransomware has made headlines throughout 2021 and continues to make news in 2022.
You may have heard about attacks on large companies, organizations, or government agencies, or perhaps you've been the victim of a ransomware attack on your own device. It's a big problem and a scary prospect to have all your files and data held hostage until you pay up. If you want to learn more about this threat, read on to learn about the different forms of ransomware, how you get them, where they come from, who they target, and finally, what you can do to protect yourself from them.
A chapter is dedicated to Ransomware attacks in order to better explain it and protect yourself as much as possible.
Fileless Malware
Fileless Malware is a type of malware that uses legitimate programs to infect a computer. They do not rely on files and leave no fingerprints, making them difficult to detect and remove.
Modern adversaries know the strategies organizations use to try to block their attacks, and they are designing increasingly sophisticated and targeted malware to evade defenses. It's a race against time, because the most effective hacking techniques are usually the newest.
The notion of malicious code residing only in memory certainly existed before the 21st century. Yet it wasn't until the prolific "Code Red" worm left its mark on the Internet in 2001 that the term "fileless malware" entered common parlance.
The first public reference I could find was in the summer of 2001, when Kaspersky Labs posted an announcement quoting none other than Eugene Kaspersky:
"We predict that in the very near future, fileless worms like Code Red will become one of the most widespread forms of malware, and the ineffectiveness of antivirus in the face of such a threat only invites danger ."
Code Red exploited a vulnerability in Microsoft IIS web servers, remaining only in the memory of the infected host.
A year and a half later, another worm - SQL Slammer - spread like wildfire by exploiting a vulnerability in Microsoft SQL servers.
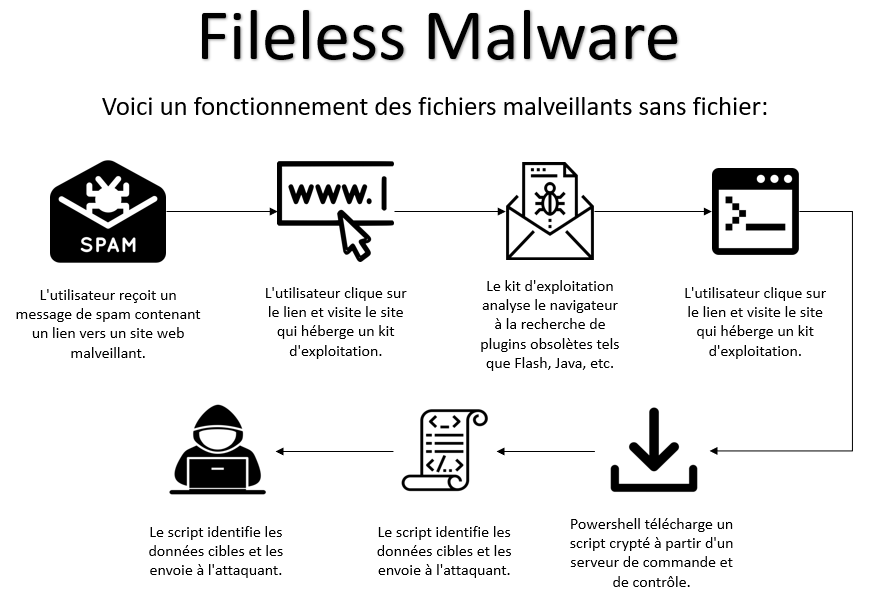
Functioning
Fileless malware attacks use existing vulnerabilities to infect a system. The attacker takes advantage of vulnerable software already installed on a computer to infiltrate, take control and carry out his attack. Unlike traditional malware, fileless malware does not need to install or download malware to infect the victim's machine.
Instead, the malware uses a system's own files and services to allow an attacker to access a device. Once inside the system, the attacker can access native operating systems such as Windows PowerShell and Windows Management Instrumentation (WMI) to carry out their malicious activity. Because many security technologies rely on these utilities, malicious activity can easily go unnoticed because analysts assume most actions are legitimate.
Fileless malware only exists in a computer's random access memory (RAM), meaning nothing is ever written directly to the hard drive. This makes them harder to detect because there are no stored files for defensive security software to scan. Additionally, security teams have little physical evidence to investigate after identifying a breach. However, because fileless malware runs in the computer's RAM and is never permanently saved to the hard drive, attackers have a smaller window of opportunity to execute the attack. When a system is rebooted, an attack using fileless malware must also be restarted.
Process
Spyware
Spyware comes from the 2 English words: Spy (to spy) and Malware and it is therefore malicious spyware.
Spyware is maliciously behaved software that aims to collect information about a person or organization and send it to another entity in a way that harms the user, such as violating their privacy or endangering the security of your device. This behavior can be present in both malware and legitimate software. Websites can engage in spying behaviors like web tracking. Hardware devices may also be affected.
And while the term "spyware" is usually reserved for malware, it's worth noting that not all software that tracks your web activity does so for the wrong reasons. Some online tracking software is used to remember your login information or to personalize your visit to the site.
Types de Spyware
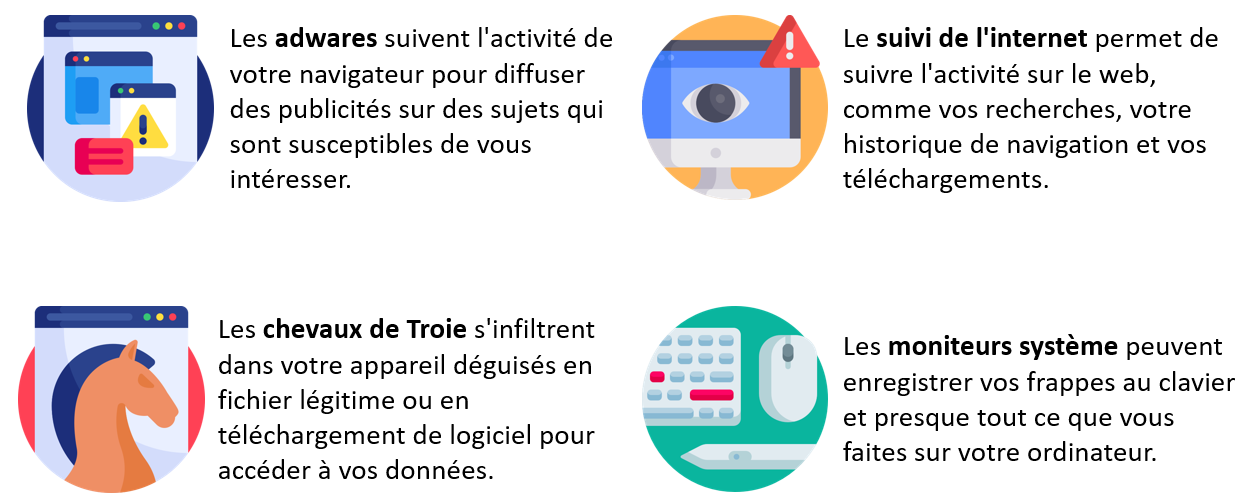
There are four common types of spyware. Their function ranges from tracking your browser activity so marketers can target your interests, for example, to monitoring your keystrokes and almost everything you do on your device. Here are some of the unique tactics that each type of spyware uses to track you:
Adware tracks your browser history and downloads in an attempt to predict products or services of interest to you. They are used for marketing purposes.
Trojans or Trojans are a type of malware disguised as legitimate software. Much like the Trojan horse of Greek mythology, a Trojan horse tricks you into letting it in (or, more precisely, installing it on your device), by acting like a software update or file. It then damages, disrupts or steals your data.
Internet Tracking is a common practice used to track your web activities, such as browsing history and downloads, primarily for marketing purposes.
System monitors are a type of spyware that can capture just about everything you do on your computer. They can record all your keystrokes, emails, chat room dialogues, websites visited and programs run. System monitors are often disguised as freeware.
Worms
A computer worm, in English called WORM, is a self-contained malicious computer program that replicates itself in order to spread to other computers.
The worm often uses a computer network to spread, relying on security failures in the target computer to gain access. It will use this machine as a host to scan and infect other computers. When these new computers invaded by the worm are controlled, it will continue to scan and infect other computers using those computers as hosts, and this behavior will continue.
Computer worms use recursive methods to copy themselves without a host program and distribute themselves according to the law of exponential growth, thereby controlling and infecting more and more computers in a short time. Worms almost always cause at least some network damage, if only by consuming bandwidth, while viruses almost always corrupt or modify the files on a targeted computer.
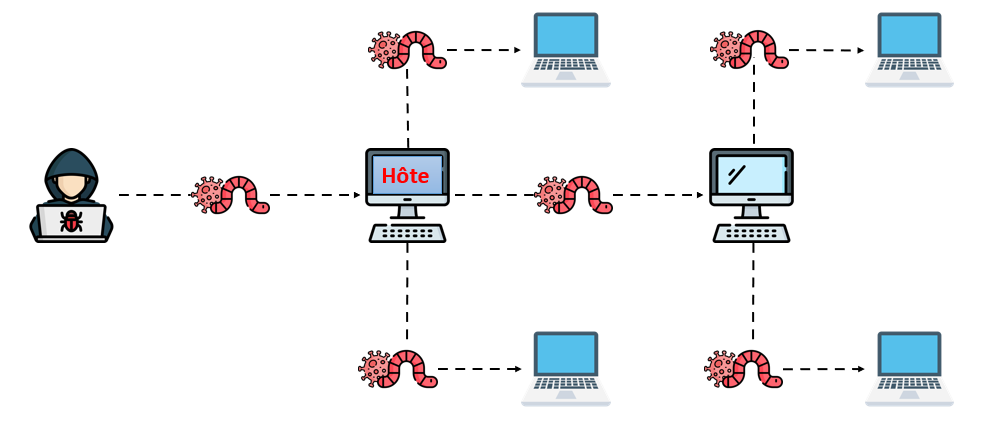
Method of propagation
Phishing: Scam emails that appear genuine may contain worms in corrupted attachments. These emails may also invite users to click on malicious links or visit websites designed to infect users with worms.
Spear-Phishing: Targeted phishing attempts can carry dangerous malware like cryptocurrencies like ransomware.
Networks: Worms can self-replicate across networks via shared access.
Security Vulnerabilities: Certain variants of worms can infiltrate a system by exploiting software vulnerabilities.
File Sharing: P2P file networks can carry malware like worms.
Instant Messaging (IM): All types of malware, including worms, can be spread through text messages and instant messaging platforms such as Internet Relay Chat ( IRC).
External devices: Worms can infect USB drives and external hard drives.
Goals
Once a computer worm has penetrated your computer's defenses, it can perform several malicious actions:
Dropping other malware like spyware or ransomware.
Consume bandwidth.
Delete files.
Overload networks.
Steal data.
Open a backdoor.
Destroy hard drive space.
Virus VS Worm
Popular thinking tends to believe that a virus and a worm are a single malware entity.
Certainly the behavior of the two is similar and their objectives too, but an essential difference exists: viruses depend on human action to be activated and need a host system to replicate. In other words, a virus can only harm your system if you run it.
For example, a virus on a USB stick connected to your computer will not harm your system if you don't activate it. And as mentioned above, a worm does not need a host system or user action to spread.
Bots
A “bot” (short for “robot”) is software that performs automated, repetitive, predefined tasks. Bots typically imitate or replace the behavior of human users.
Since they are automated, they operate much faster than human users. They perform useful functions, such as customer service or search engine indexing, but they can also come in the form of malware - used to take complete control of a computer.
Difference Between Good and Bad Bot
Computer bots and Internet bots are essentially digital tools and, like any tool, they can be used for good or bad purposes.
Good bots perform useful tasks, but bad bots - also known as malicious bots - carry risks and can be used to hack, spam, spy, disrupt and compromise websites of all sizes. It is estimated that today, up to half of all internet traffic consists of computer bots performing certain tasks, such as automating customer service, simulating human communication on social networks, business help with online content research and search engine optimization assistance.
According to "Bad Bot Report" relayed by CPOMagazine in their article: Bad Bot Traffic Report, more than 40% of internet usage comes from Bots, therefore 27% from bad Bots.
Organizations or individuals use bots to replace repetitive tasks that a human would otherwise have to perform. The tasks performed by bots are generally simple and completed at a much faster pace than human activity.
Not all tasks performed by bots are benign – bots are sometimes used for criminal activities such as data theft, scams, or DDoS attacks.
Examples
While malicious bots create problems and challenges for organizations, dangers for consumers include their potential to carry out data and identity theft, keylogging of sensitive information such as passwords, bank details and addresses, and phishing.
Malicious bots can easily go unnoticed. They hide easily on a computer and often have similar or even identical file names and processes to regular system files or processes.
Here are some examples of malicious bots:
Spambots
Spambots can harvest email addresses from contact pages or guestbooks. They may also post promotional content in forums or comment sections in order to attract traffic to specific websites.
Malicious Chatterbots
Dating websites and apps are havens for malicious chatbots. These bots pretend to be a person, imitating human interaction, and often trick people into not realizing they are chatting with harmful programs whose goal is to obtain personal information, including credit card numbers, of unsuspecting victims.
File sharing bots
These bots take the user's query term (e.g. a popular movie or an artist's album) and respond to the query by indicating that they have the file to download and providing a link. The user clicks the link, downloads and opens the file, and unknowingly infects their computer.
Credential stuffing
These are bots that "stuff" known usernames and passwords (usually from data breaches) into online login pages in order to gain unauthorized access to user accounts.
DoS or DDoS bots
This is excessive bot traffic used intentionally to overwhelm a server's resources and prevent a service from functioning.
DoS & DDoS attack:
A denial of service attack (DoS attack) is a computer attack aimed at making a service unavailable and preventing legitimate users of a service from using it.
Currently the vast majority of these attacks are carried out from several sources, we then speak of a distributed denial of service attack (DDoS attack for Distributed Denial of Service attack).
Definition: WIKIPEDIA
Mobile Malware
Mobile malware is malware specifically designed to target mobile devices, such as smartphones and tablets, with the aim of accessing private data.
Although mobile malware is not currently as prevalent as malware that attacks traditional desktops, it is a growing threat as many companies now allow employees access to corporate networks using their personal devices, which can bring unknown threats into the environment.
Types of Malware on Mobile
Cybercriminals use various tactics to infect mobile devices. If you're looking to improve your protection against mobile malware, it's important to understand the different types of mobile malware threats. Here are some of the most common types:
Remote Access Tools (RATs) provide extensive access to data from infected victim devices and are often used for intelligence gathering. RATs can typically access information such as installed applications, call history, address books, Internet browsing history, and SMS data. RATs can also be used to send text messages, activate device cameras, and record GPS data.
Banking Trojans are often disguised as legitimate applications and seek to compromise users who conduct banking transactions - including money transfers and bill payments - from their mobile devices. This type of Trojan aims to steal login data and financial passwords.
Ransomware is a type of malware used to lock a user's access to their device and demand payment of a "ransom", usually in untraceable bitcoins. Once the victim pays the ransom, they are provided with passcodes to unlock their mobile device.
Cryptomining Malware allows attackers to secretly run calculations on a victim's device - allowing them to generate cryptocurrencies. Cryptomining is often carried out through Trojan code hidden in legitimate-looking applications.
Click-through fraud is a type of malware that allows an attacker to hijack a device to generate revenue through fake click-throughs.
Distribution
There are several ways that attackers distribute their malicious code, but the most commonly used are:
Mobile Phishing and Identity Theft:
Phishing (see PHISHING in Capsule 1) is the practice of tricking someone into providing valuable personal information or account data, often through identity theft. .
Identity theft involves disguising an electronic communication or website as an entity the victim trusts. While identity theft and phishing often go hand in hand, identity theft can be used for nefarious purposes other than phishing for account information. For example, a spoofed email may attempt to convince the recipient to click on a malicious link.
While phishing has traditionally focused on acquiring credentials through email, phishing through SMS messages (smshishing) and messaging apps has become much more prevalent. In fact, 57% of organizations have experienced a mobile phishing attack. This shouldn't be too surprising when you consider the fact that people are 18 times more likely to click on a suspicious link on a mobile device than on a desktop computer.
One of the most common methods to trick victims into installing malware is to send them, via SMS, links to Android Package (APK) files hosted on websites controlled by attackers. For example, victims may be asked to click on an SMS link to a spoofed banking site, designed to appear trustworthy and convince the victim to "update their banking app." The update then installs the malicious code, allowing the attacker to gain access and collect credentials.
Last updated