Malware - Ransomware
This part will define ransomware, explain its origin as well as its evolution over the years, and give instructions on how to protect yourself and detect an attack.
Definition
Ransomware, also called ransomware or ransomware, is a type of malware that prevents users from accessing their system or personal files and demands payment of a ransom in order to regain access.
While some people might think "a virus has locked my computer", ransomware is generally classified in a different category of malware than viruses.
The first ransomware variants were developed in the late 1980s, and payment had to be sent by postal mail. Today, ransomware perpetrators order payment to be sent by cryptocurrency or credit card, and attackers target individuals, businesses, and organizations of all kinds. Some ransomware authors sell the service to other cybercriminals, which is known as Ransomware-as-a-Service or RaaS.
History
The starting point
The first known example of ransomware is the AIDS Trojan software, also known as Aids Info Disk or PC Cyborg Trojan, which was created in 1989 by a group of hackers called "The AIDS Information Team". This malware spread via a floppy disk and once installed on the victim's computer, it displayed a message asking the user to pay a ransom of $189 to unlock the computer.
The purpose of the AIDS Trojan was to raise money for HIV/AIDS research according to one of its authors Dr. Joseph Popp, but the software was widely criticized for using dishonest methods to collect money. Although the AIDS Trojan was the first known example of ransomware, it did not have a significant impact on the world of cybersecurity at the time and was not really considered true malware.
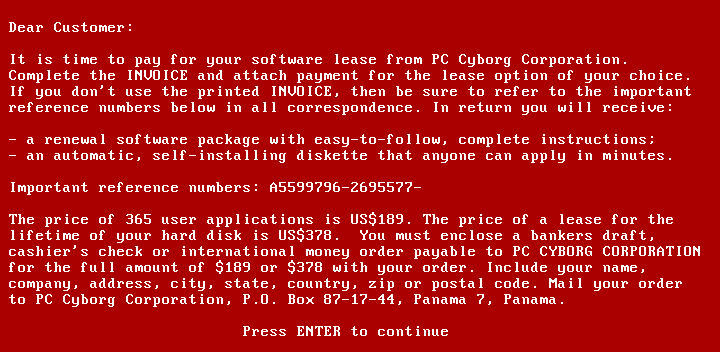
The AIDS Trojan was malware that spread via an infected floppy disk. Once installed on the victim's computer, it modified the AUTOEXEC.BAT file, which prevented the computer from booting properly. When the user restarted their computer, they would see a message asking them to pay a ransom of $189 to unlock their computer.
AUTOEXEC.BAT:
AUTOEXEC.BAT is the name of a system file originally encountered in the MS-DOS operating system. This is a batch file of type .bat (command file in text format) located at the root of the device on which the computer starts. The name of the file comes from the concatenation of the words automatic and execution, thus describing its function which is to automatically execute commands upon system startup. The word AUTOEXEC was also created in order to respect the naming rule of the FAT file system which imposes an 8.3 format (i.e. 8 characters, a period, 3 characters).
Definition: WIKIPEDIA
Since then, more sophisticated malware families have emerged, such as GpCode in 2004, which was spread via malspam campaigns and whose victims were asked to use gift cards like Ukash to pay the ransom. This malware encrypted files like current ransomware, but it contained cryptographic flaws that made the recovery process rather easy.
MalSpam: Malicious spam (malspam) is unsolicited email that seeks to deliver a malicious payload, either through a Microsoft Office attachment or by tricking the user into clicking a link in the email.
Around 2011, a new ransomware threat appeared: Reveton (police ransomware). This malware did not encrypt files but locked victims' screens, displaying a threatening police warning and asking users to pay a fine with prepaid gift cards like Paysafecard and MoneyPak. The warning was localized in different languages and used relevant police logos, making the situation more realistic for victims.

Bitcoin et Ransomware
Cybercrime - a broad category of malicious activity that includes all types of cybercriminal attacks, including malware, banking Trojans, ransomware,... - has seized the monetization opportunity created by bitcoin. This resulted in a significant proliferation of ransomware starting in 2012.
BITCOIN:
Bitcoin is a peer-to-peer technology operating without a central authority. Transaction management and bitcoin creation is handled collectively by the network. Bitcoin is free and open. Its design is public, no one owns or controls Bitcoin and anyone can join. Thanks to several of its unique properties, Bitcoin makes promising uses possible that could not be covered by previous payment systems.
Definition: BITCOIN.ORG
However, this ransomware business model remains imperfect because while bitcoin payments are easy transactions for cybercriminals to use, they are not always as easy for their non-tech-savvy targets to navigate. To guarantee payment, some criminals have gone so far as to open call centers to provide technical support and help victims sign up for Bitcoin – but this takes time and costs money.
When Bitcoin began to gain popularity, ransomware developers realized that this was the method of monetary extraction they were looking for. Bitcoin exchanges have provided adversaries with a means to receive instant payments while maintaining anonymity, all transacted outside the strict confines of traditional financial institutions.
Here is a non-exhaustive list of known ransomware and how they work:
Cryptolocker (2013): This ransomware encrypted the user's files and demanded a ransom to decrypt them. It was usually spread via spam emails containing infected attachments.
WannaCry(2017): This ransomware was one of the largest in history in terms of scope and damage caused. It spread rapidly globally by exploiting a security vulnerability in Windows systems. It has caused significant disruption to hospitals, businesses and other organizations.
NotPetya (2017): This ransomware spread mainly in Ukraine by posing as an update to the accounting software popularized in the country. It quickly spread its infection to other countries, causing significant disruption to businesses and organizations.
LockerGoga (2019): This ransomware primarily targeted businesses and organizations, causing significant disruption to their operations. It has been used in "ransomware" attacks aimed at encrypting user files and demanding a ransom to decrypt them.
Ryuk(2019): This ransomware mainly targets businesses and organizations and demands a large ransom to decrypt files. It has been involved in numerous high-profile software ransom attacks.
Consequences of an attack
Income
A ransomware attack can seriously impact an organization's ability to operate. Even if the organization is well prepared and has working backups, restoring affected systems can take hours. Worse yet, organizations that were not as well prepared, or whose backups may have been compromised during the attack, may take days or weeks to return to full operational capacity, meaning their revenue will decline or stop completely while they recover.
Reputationv
A data breach or ransomware attack can damage a company's reputation. Some customers may view a successful attack as a sign of weak security practices, or be so severely affected by a service outage that they choose to change companies.
Financier
Ransomware comes with unexpected costs and is expensive. In addition to the loss of revenue an organization may incur, there are other costs that may be obvious and others that may not. The most obvious costs are: the cost of paying the ransom (if paid); the cost of remediating the incident, including new hardware, software and incident response services; insurance deductibles; attorney fees and litigation; and public relations. Other less obvious costs may include: increased insurance premiums, devaluation of reputation/family name and loss of intellectual property.
Data
In a ransomware attack, a malicious actor encrypts many files, rendering them and the systems that depend on them unusable. If a ransom is not paid, these encrypted files are often permanently locked, forcing the organization to regenerate the information, if it can. However, even if a ransom is paid, there is no guarantee that a threat actor will act benevolently and provide a decryption key. Additionally, even if a key is provided, it is still possible that the ransomware attack caused significant destructive damage, which may require rebuilding affected systems anyway. Additionally, if the threat actor stole a trade secret, proprietary information, or personally identifiable information (PII), the loss of that data could give rise to legal action or result in loss of competitive advantage .
Attack vectors
By email
Phishing attacks are one of the most common delivery systems for ransomware. In these attacks, hackers successfully convince a person to click on a link or open an attachment who then downloads the ransomware to their system. This attack vector often takes the form of social engineering in which cybercriminals pose as someone the recipient trusts and trick them into granting administrative access to company systems.
There are different techniques:
Phishing links embedded in the body of the message
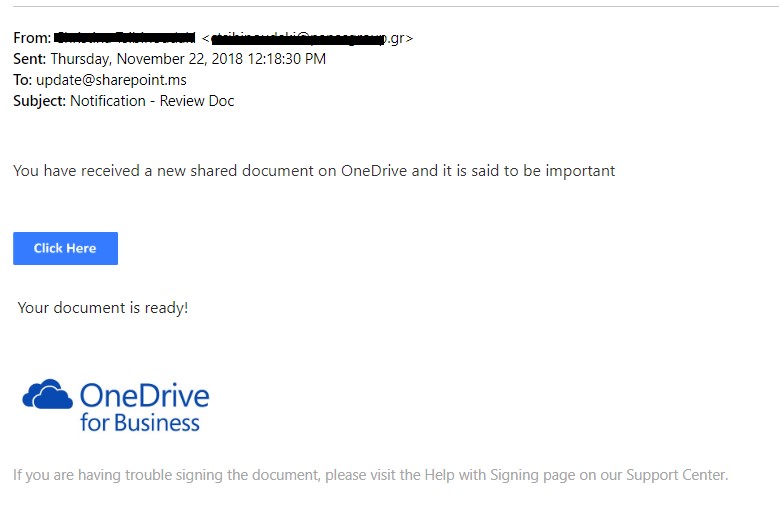
Malicious attachments
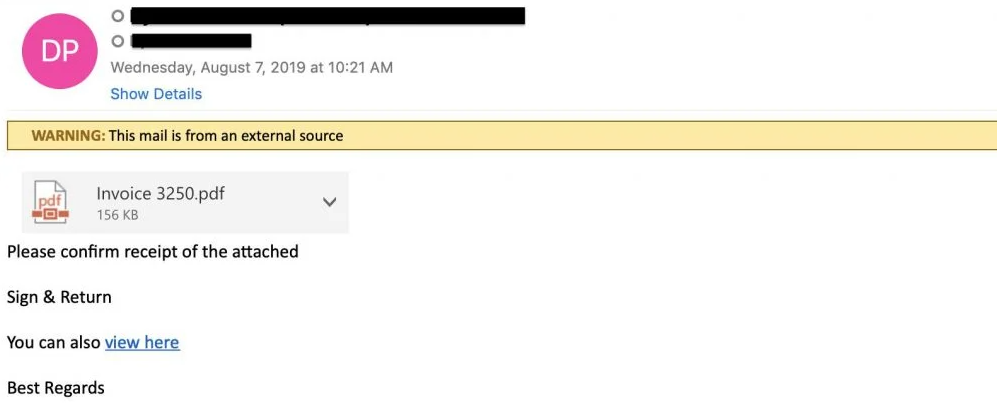
Pages Web
Malicious ransomware code can also be found in web scripts hidden on seemingly legitimate or compromised sites. This is a perfect attack vector for cybercriminals because victims believe they are visiting a trusted site. When a person visits this site, the code is automatically downloaded, and once executed, it can infect the user's system and move laterally through the organization, encrypting files and data.
Pop-ups
Advertisements and pop-ups are another common vector for ransomware attacks on the Internet. They may appear genuine, but like phishing schemes, they can trick people into clicking on them by pretending to be a trusted brand. At that point, they either direct the user to a new open window containing malicious links or automatically download ransomware or other forms of malware onto the user's computer.
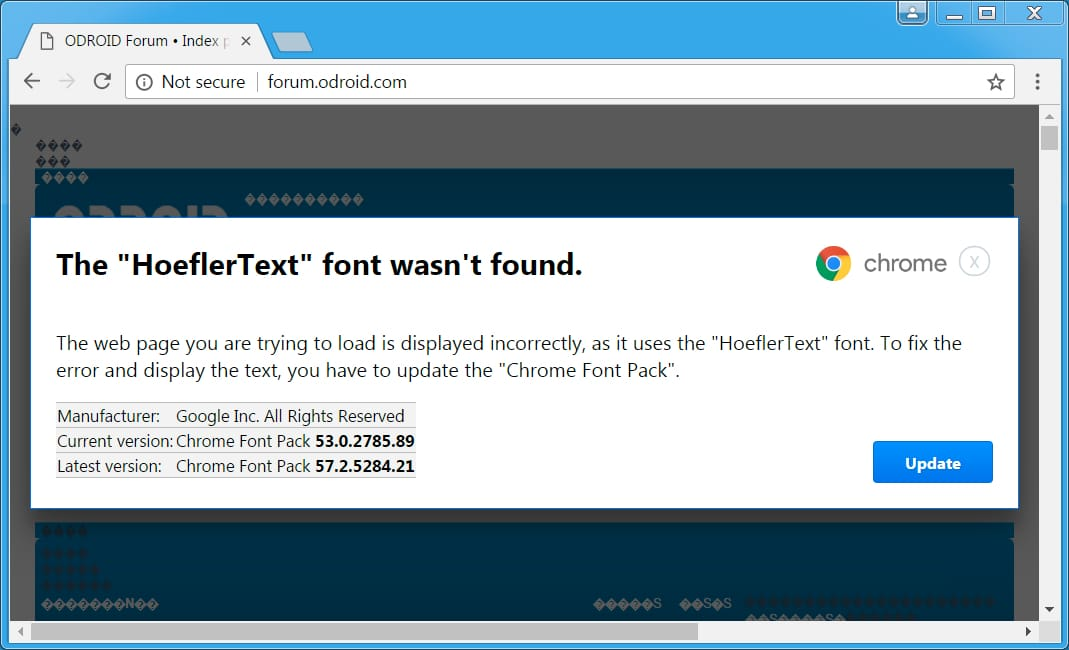
Instant messages
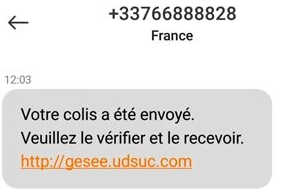
As users become more aware of email phishing, hackers have turned to instant messaging platforms such as WhatsApp, Slack, Snapchat, Facebook Messenger and Microsoft Teams to carry out smishing campaigns. These threats work in much the same way as email attacks, where the ransomware is launched when a user clicks on a link or attachment from a sender posing as a reputable company.
Many organizations have blocked these platforms in the past, but with the rise of remote working habits, instant messaging has become an essential collaboration tool for businesses around the world, making these attacks difficult to avoid.
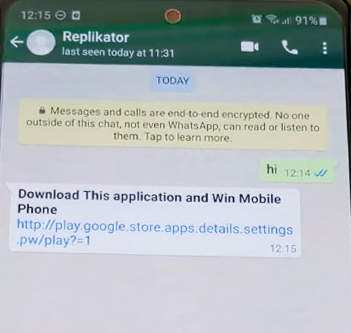
Text Messages
Text messages are an extremely popular vector for ransomware. Spam, impersonation, and phishing messages are the main culprits, with attackers often using ransomware-as-a-service or malware-for-hire to easily and cheaply execute ransomware attacks. When a user clicks on a link, the ransomware is downloaded to their device and can spread to everyone in their contact list, including coworkers.
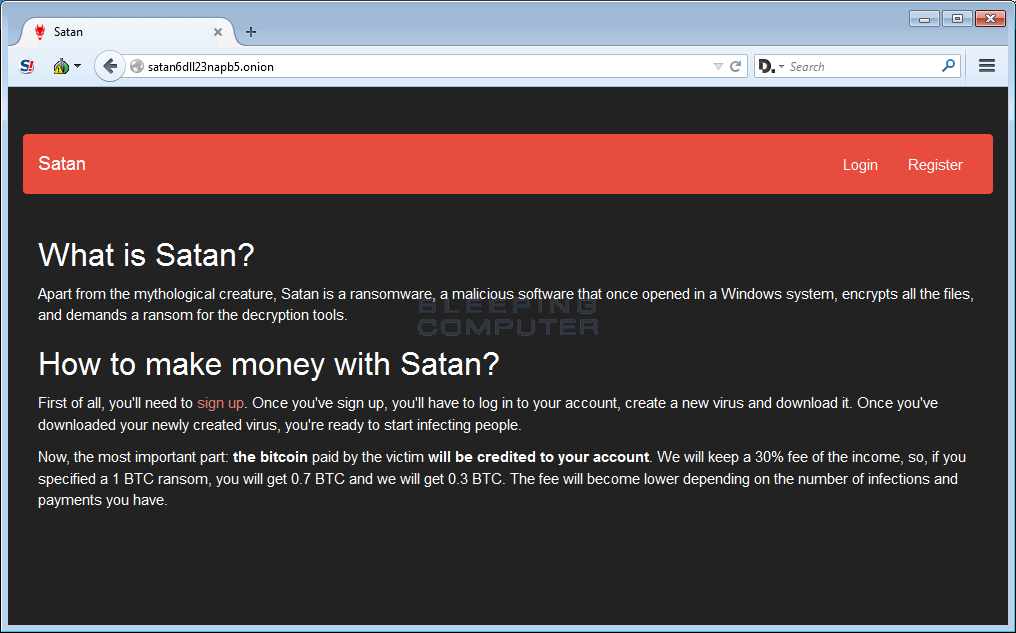
Ransomware as a Service (RaaS)
Ransomware as a Service (RaaS) is a business model between ransomware operators and affiliates in which affiliates pay to launch ransomware attacks developed by the operators. The ransomware service is a variation of the SaaS (Software as a Service) business model.
SaaS ou Software as a Service:
Software as a service (SaaS), or software as a service, is a commercial exploitation model of software in which it is installed on remote servers rather than on the user's machine. Customers do not pay a user license for a version, but freely use the online service or, more generally, pay a subscription.
Definition: WIKIPEDIA
RaaS kits allow affiliates who don't have the skills or time to develop their own ransomware variant to get up and running quickly and affordably. They are easy to find on the dark web, where they are advertised in the same way as goods on the legal web.
A RaaS kit can include 24/7 support, bundles, user reviews, forums, and other features similar to those offered by legitimate SaaS providers. RaaS kits range in price from $40 per month to several thousand dollars - insignificant amounts, considering that the average ransom demand in 2021 was $6 million. A threat actor does not need every attack to be a success to enrich themselves.
There are four common RaaS revenue models:
Monthly subscription for a fixed amount
Affiliate programs, which are the same as the monthly fee model but where a percentage of the profits (usually 20-30%) go to the ransomware developer
Single license fee without profit sharing
Pure and simple profit sharing
The most sophisticated RaaS operators offer portals that allow their subscribers to view infection status, payment totals, total encrypted files, and other information about their targets. An affiliate can simply log into the RaaS portal, create an account, pay with bitcoins, enter details about the type of malware they want to create, and click the submit button. Affiliates may have access to the same support, communities, documentation, feature updates, and other benefits as subscribers to legitimate SaaS products.
Responding to a Ransomware attack
Stay calm and thoughtful
It's hard to stay calm when you can't access important files on your computer. But the first step you should take after being hit by ransomware is to not panic and keep your cool.
Most people rush to pay the ransom before analyzing the seriousness of the situation they find themselves in. Staying calm and taking a step back can sometimes open doors to negotiations with the attacker or resolving the problem without even paying.
Take a photo/screenshot
of the ransomware note The second step is to immediately take a photo of the ransomware note on your screen using your smartphone or a camera. If possible, also take a screenshot on the affected machine.
This will help you file a police report and speed up the recovery process.
Raccourci sur windows pour faire un screenshot:
WINDOWS+SHIFT+S

Quarantine affected systems
It is important to isolate affected systems as soon as possible. Ransomware typically scans the target network and spreads laterally to other systems.
It is best to separate affected systems from the network to contain the infection and prevent ransomware from spreading.
Search for decryption tools
Fortunately, many decryption tools are available online, on sites such as No More Ransom.
If you already know the strain name of your ransomware, simply enter it from the web and search for the corresponding decryption key. The list is not alphabetical, and the site adds new decryption tools at the bottom of the list.
Disable maintenance tasks
You should immediately disable automated maintenance tasks, such as deleting temporary files and rotating logs, on affected systems. This will prevent these tasks from interfering with files that might be useful for forensic analysis and investigation.
Forensic analysis:
Forensic analysis (more frequently called “forensic”) consists of investigating an information system after a cyberattack. The analysts will collect all the raw data (deleted files, hard drives, backups, system logs, etc.), study it to understand what happened and draw conclusions. This task, sometimes arduous, makes it possible to produce evidence necessary for internal action or the launch of legal proceedings, for example.
Definition: TEHTRIS
Disconnect backups
Most modern ransomware strains immediately attack backups to thwart recovery efforts.
It is therefore imperative for you or your company to secure your backups by separating them from the rest of the network. You should also lock access to backup systems until the infection is eliminated.
Report ransomware
As soon as you notice a ransomware attack, be sure to contact law enforcement.
Ransomware is a crime and should be reported to local law enforcement. Even if law enforcement can't help you decrypt your files, they can at least help other people avoid a similar fate.
Information: Belgique / France
Deciding whether to pay or not
Deciding to pay for ransomware is not an easy decision and comes with pros and cons. Only pay if you have exhausted all other options and losing data is more damaging to you or your business than paying the ransom.
Protection against ransomware: The right reflexes
Never click on dangerous links
Avoid clicking on links in spam messages or on unknown websites. If you click on malicious links, an automatic download may be initiated, which could result in your computer being infected.
Avoid disclosing personal information
If you receive a call, text message or email from an untrusted source asking for personal information, do not respond. Cybercriminals planning a ransomware attack may try to collect personal information in advance, which is then used to tailor phishing messages specifically for you. If you have any doubts about the legitimacy of the message, contact the sender directly.

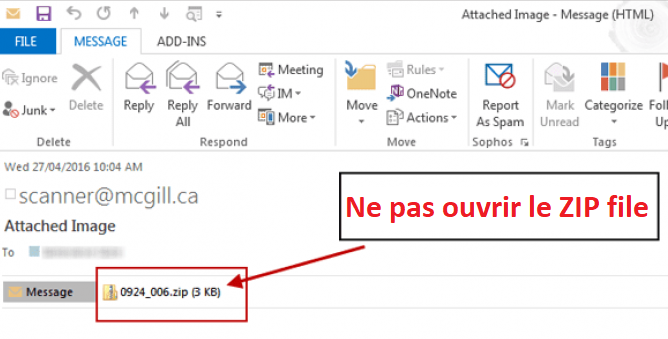
Do not open attachments from a suspicious email
Ransomware can also find its way to your device through email attachments. Avoid opening any suspicious-looking attachments. To make sure the email is trustworthy, pay close attention to the sender and verify that the address is correct. Never open attachments that prompt you to run macros to view them. If the attachment is infected, opening it will cause a malicious macro to run that gives the malware control of your computer.
Never use unknown USB drives
Never connect USB drives or other storage media to your computer if you do not know where they came from. Cybercriminals may have infected the storage media and placed it in a public place to trick someone into using it.

Keep your programs and operating system up to date
Regularly updating programs and operating systems helps protect you from malware. When you update, make sure you have the latest security patches. This will make it more difficult for cybercriminals to exploit vulnerabilities in your programs.

The technical term used is patch management.
Patch Management: Patch management involves identifying and deploying software updates, also called “fixes” or “patches,” to various endpoints, including computers, mobile devices, and servers.
Patches are typically distributed by software developers to fix known security vulnerabilities or technical issues. They also allow you to add new features and functions to the application. These short-term solutions are intended to be used until the next version of the software is released.
Definition: Crowdstrike
Use only known download sources
To minimize the risk of downloading ransomware, never download software or media files from unknown sites. Trust verified and trustworthy sites for downloads. Websites of this type can be recognized by trust seals. Make sure the browser address bar of the page you are visiting uses "https" instead of "http." A shield or lock symbol in the address bar can also indicate that the page is secure. Also use caution when downloading anything to your mobile device. You can trust the Google Play Store or the Apple App Store, depending on your device.
Use VPN services on public Wi-Fi networks
Conscientious use of public Wi-Fi networks is a wise protection measure against ransomware. When you use a public Wi-Fi network, your computer is more vulnerable to attacks. To stay protected, avoid using public Wi-Fi for sensitive transactions or use a secure VPN service.
Belgium: Report an attack
It is possible to file a complaint with the local police and report the incident to CERT.be via [email protected] indicating the type of data carrier, operating system, mode of infection, name ransomware, payment method and, if possible, providing screenshots of the infected computer system. This action can contribute to the fight against cybercrime internationally, although it does not always guarantee a solution to ransomware infection.

France: Report an attack
"This teleservice can only be used if you are an individual and if you file a complaint in your own name.
Even if you file a complaint online, you can request to meet with an investigator. The investigator may also decide to interview you if he considers it necessary." Message from the Ministry of the Interior.
Last updated