Phishing - Origins
Etymology
Phishing scams use spoofed e-mails and websites as bait to lure people into voluntarily disclosing sensitive information. The term phishing is a contraction of the English words “fishing” and “phreaking”, meaning the exploration, experimentation and study of telecommunication systems.

Phishing sur America Online
In the 90s, AOL, formerly known as America Online, was one of the world's leading Internet service providers, with over a million customers subscribing to its service. AOL's massive popularity attracted the attention of hackers. People trading in pirated and illegal software and tools used AOL for their communications.

Phishers first carried out attacks by stealing users' passwords and using algorithms to create random credit card numbers. While the chances of success were rare, they did hit the jackpot quite often, and caused a great deal of damage. Random credit card numbers were used to open AOL accounts. These accounts were then used to spam other users and for a host of other scams.
Spammer: Anglicism. To send mass e-mail messages to unsolicited persons for advertising or commercial purposes. (Definition by “LeRobert”)
AOL put an end to this practice in 1995, when the company introduced security measures to prevent the use of randomly generated credit card numbers.
New technique against AOL
After putting an end to their credit card extortion, the phishers created what would become a very common and long-lasting set of techniques. Using AOL's instant messaging and e-mail systems, they would send messages to users pretending to be AOL employees.
These messages asked users to verify their account or confirm their billing information. More often than not, people fell for it; after all, nothing like this had ever been done before. The problem intensified when phishers created AIM (AOL Instant Messenger) accounts via the Internet; these accounts could not be “punished” by AOL's terms of use service.
AOL Instant Messenger (AIM): A computerized instant messaging and presence program created by AOL, enabling registered users to communicate in real time.
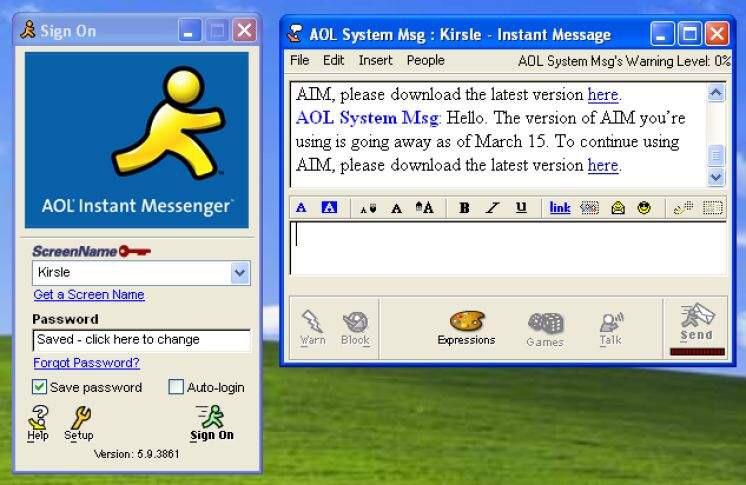
Finally, AOL was forced to include warnings on its e-mail and instant messaging clients to prevent people from providing sensitive information via this channel.
Last updated