Malware - Origines
Etymology
As software designed to disrupt the normal operation of a computer, malware is a general term for viruses, Trojan horses, and other destructive computer programs used by threat actors to infect systems and networks in order to access sensitive information or block the system completely.
The word malware comes from the English MALICIOUS SOFTWARE which means “malicious software”. In French, we find the term Maliciel which is short for Malicious Software.

Early malware was primitive, often spreading entirely offline via floppy disks carried from computer to computer by human hands. With the development of networks and the Internet, malware authors were quick to adapt their malicious code and take advantage of this new means of communication.
Here is a representative list of some of the important early malware releases and their impact on the world.
Creeper - 1971
An experimental computer network, ARPANET, was created in 1969 and was the precursor to the Internet. It was designed to send computer-to-computer communications over long distances, without the need for a dedicated telephone connection between each computer. To achieve this required a method of splitting and sending data, known today as packet switching. Its first users, few in number, were mostly computer scientists.
ARPANET:
"Advanced Research Projects Agency Network" is the acronym for the first data packet transfer network designed in the United States by the Defense Advanced Research Projects Agency (DARPA). The project was launched in 19662, but ARPANET did not see the light of day until 1969. Its first official demonstration dates from October 1972.
In 1983, Internet Protocol (TCP/IP) replaced NCP as the primary protocol of ARPANET. The ARPANET then became a subnetwork of the first Internet.
Definition: Wikipedia
Imagine their surprise when one day in 1971, computer screens connected by teletype displayed the phrase: “I’m the creeper, catch me if you can!”.
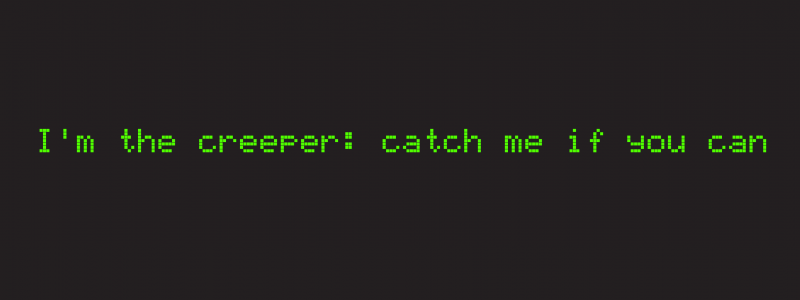
Without knowing it at the time, they were the first victims of a computer virus.
But what did this mysterious message mean, and who sent it?
It turns out that it wasn't a hacker who coded the first computer virus, and it wasn't sent with malicious intent. Bold, Beranek and Newman (now Raytheon BBN Technologies) were pioneers of packet switching networks like ARPANET and the Internet. One of its researchers, Bob Thomas, had created Creeper as an experimental computer program.
Creeper was a worm - a type of computer virus that replicates and spreads to other systems. In this case, his targets were Digital Equipment Corporation (DEC) computers that were linked to ARPANET.
But it wasn't malware like we associate with today's computer viruses; Creeper was only displaying his cryptic message. It did not encrypt files, demand ransom, destroy data, or steal information. He only displayed his provocative defiance.
Its creator had simply wanted to create an experimental program that self-destructed to show that it was possible. If he did it primarily out of scientific curiosity, he also had fun giving it a name: Creeper was a mysterious green and macabre bank robber in the famous 70s cartoon, "Scooby-Doo".

The birth of Reaper
The development of the Creeper virus gave rise to Ray Tomlinson's Reaper, the first antivirus software designed to stop threats of this type. Interestingly, Reaper itself is a computer worm programmed to delete all instances of Creeper in infected computers.
Last updated