Define the perimeter
Last updated
Last updated
The target scope tells Burp which URLs and hosts you want to test. This allows you to filter traffic generated by your browser and other sites, so you can focus on the traffic that interests you.
This site imitates the principles of a very basic social network, where you can create a user profile (pinned name, photo, message and website...), manage it and post short messages (snippets in this case ), so it is very suitable as study material.
Here is the link: https://google-gruyere.appspot.com/
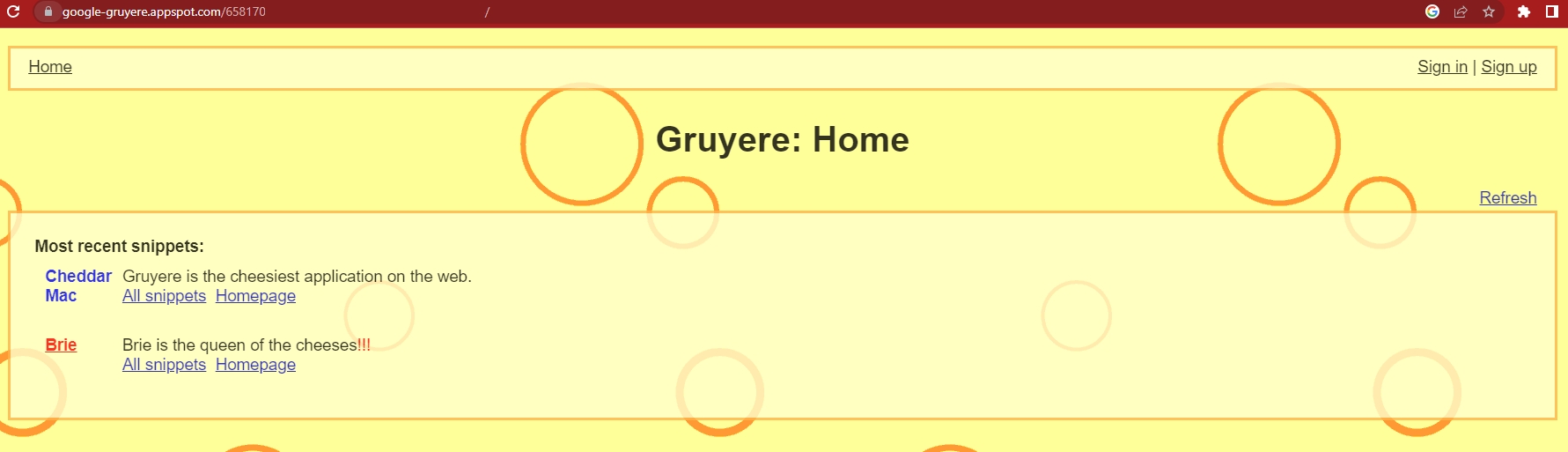
The link will direct you to your instance (see image below, behind the URL there is my instance number).
The lab shows how vulnerabilities in web applications can be exploited and how to defend against these attacks. In the lab, you will practice cross-site scripting (XSS), cross-site request forgery (XSRF),... and you will also have the opportunity to evaluate the impacts of such vulnerabilities (denial of service, disclosure of 'information, remote code execution...).
Depending on what you are using, start either the BURP browser or your FoxyProxy addon.
Then, you go to the URL of your GRUYERE via your browser:
Now try browsing the app a little by clicking on the features you see:
Sign In
Sign Up
Home
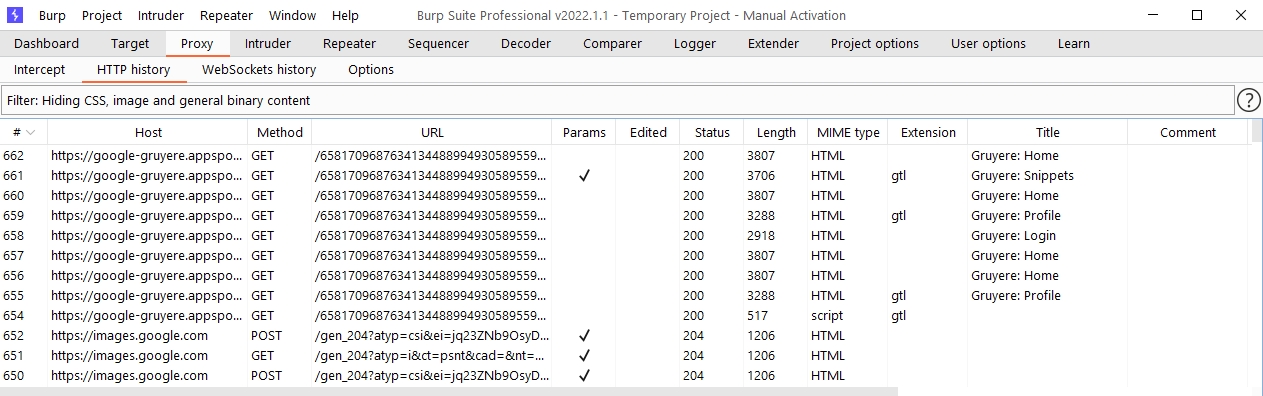
In Burp, go to the Proxy tab > HTTP History. For easier reading, continue clicking the leftmost column header (#) until the requests are sorted in descending order. This way you can see the most recent requests at the top of the screen.
Note that HTTP History displays details of every request made by the browser, including requests to third-party websites that are not of interest to you.
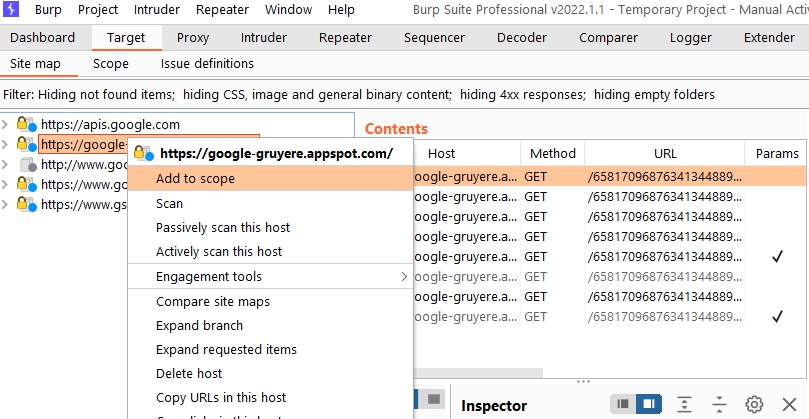
Go to Target > Site map. In the left panel, you can see a list of hosts that your browser has interacted with. Right-click on the target site node and click “Add to scope”. When prompted in a pop-up, click Yes to exclude traffic out of scope.
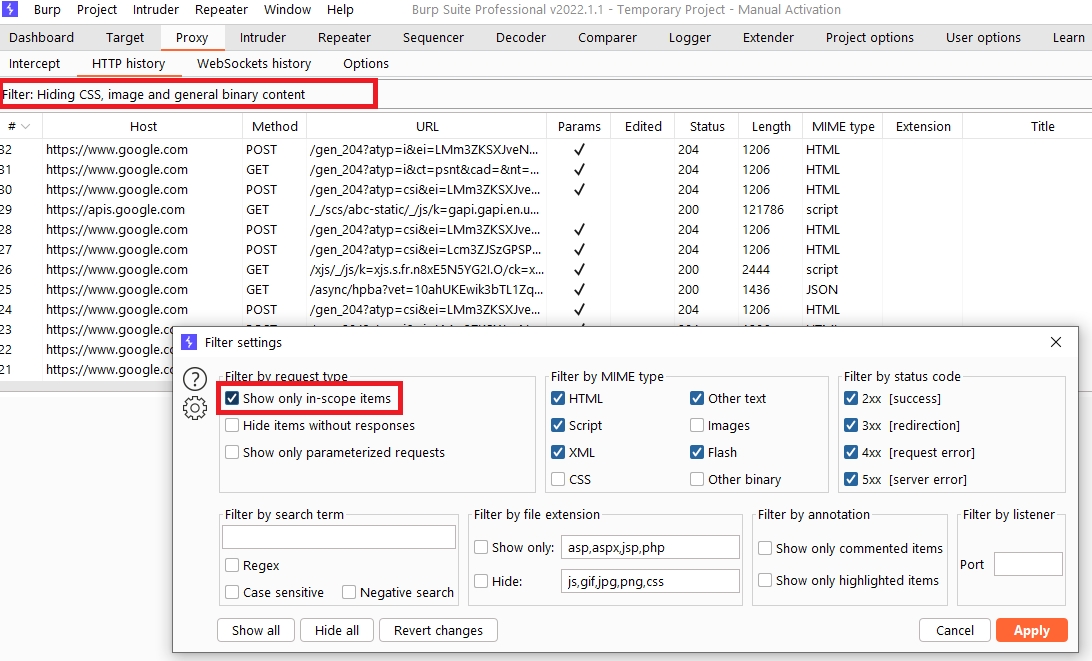
Click the display filter above HTTP History and select Show only items in scope.
Scroll through your HTTP history. Notice that it now only displays entries from the target website. All other entries have been hidden. This greatly simplifies the history, which now only contains the elements that interest you.
If you continue browsing the target site, you will notice that out-of-scope traffic is no longer recorded in the sitemap or proxy history.